I. INTRODUCTION
Accurate user authentication and authorization control are the key functions on Internet. The possessions for authentication can be stolen, broken, or forged; the passwords for authentication can be forgotten or attacked. Biometric recognition realizes authentication based on the inherent physical or behavioral characteristics of human beings [1]; which overcomes the drawbacks of the traditional authentication technologies [2].
Palmprint has rich discriminative features, including main lines, wrinkles, ridges and minutiae points. In addition, palmprint recognition can have low equipment requirements, fast speed, and high accuracy; therefore, it is widely deemed as an important biometric modality.
Video palmprint recognition (VPR) has some advantages that are absent in image palmprint recognition. In VPR, the registration and recognition can be automatically implemented without users’ manual manipulation. A good-quality image can be selected from the video frames or generated from the fusion of multiple video frames [3]. VPR in contactless mode overcomes the problems caused by contact mode.
-
Health risk: Due to the health and personal safety, it is unhygienic for users to contact the identical sensors or devices. Contact acquisition definitely increases the risk of infectious diseases, such as COVID-19.
-
Low acquisition flexibility: Contact acquisition suppresses the users’ acceptance, flexibility and comfortability.
-
Surface contamination: The surface of contact sensors can be contaminated easily, especially in harsh, dirty, and outdoor environments. The surface contamination of contact sensors is likely to degrade the quality of the subsequent acquired biometric images. In addition, the biometric features can be retained on the surface of contact sensors, which increases the risk of leaking biometric privacy.
-
Resistance from traditional customs: Some conservative nations/nationalities resist the users of different genders to contact the identical devices.
Although VPR in contactless mode overcomes the aforementioned problems, it encounters with several revere challenges such as complex background, various illuminations, uncontrollable hand placement (pose and location) [4].
This paper develops practical VPR algorithm and system. The main contributions are summarized as follows.
-
Double-line-single-point (DLSP) assisted placement technique can overcome the challenges as well as effectively reduce the localization error and computation complexity. Modified DLSP (MDLSP) technique is developed to reduce the invalid area in the frames.
-
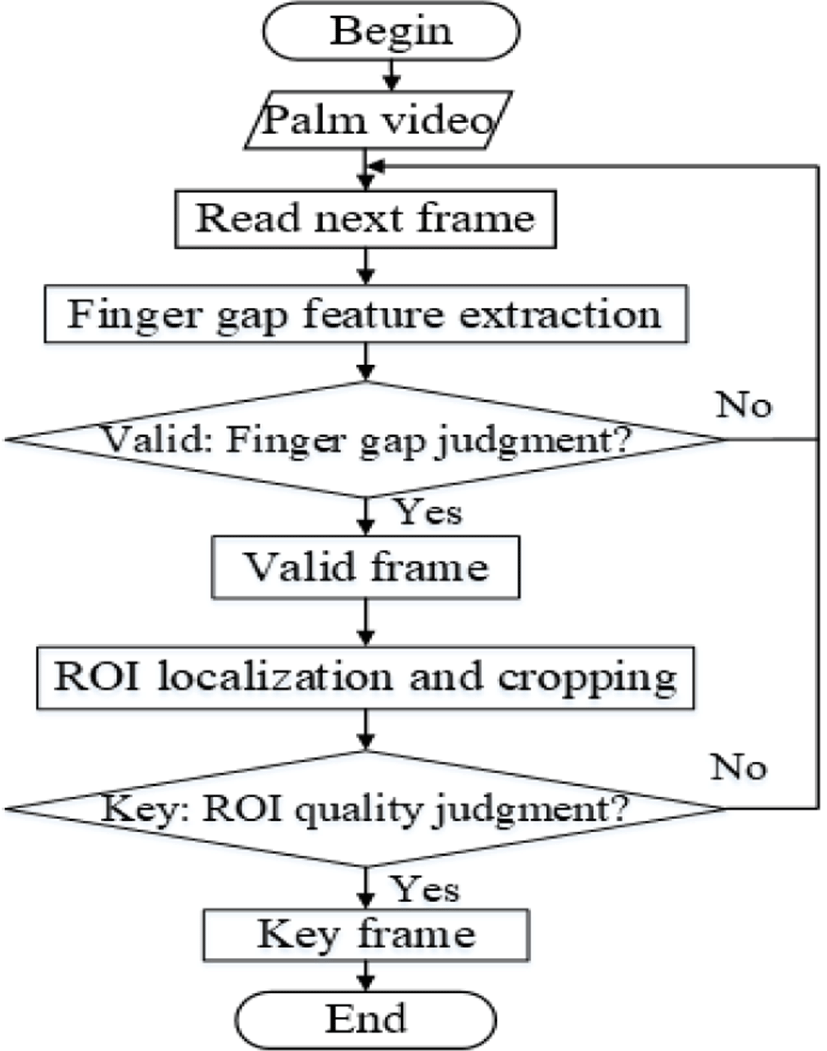
The valid frames, in which users place their hands correctly, are selected according to finger gap judgement, and then some key frames, which have good quality, are selected from the valid frames as the gallery samples that are matched with the query samples for authentication decision.
-
The VPR algorithm is conducted on the system designed and developed on mobile device.
The rest of this paper is organized as follows. Section 2 revisits the related works. Section 3 specifies the methodology. Section 4 are the experiments and discussions. Finally, the conclusions are drawn in Section 5.
II. RELATED WORKS
The purpose of palmprint image preprocessing is typically to accurately segment, localize and crop the region of interest (ROI) [5]. Palmprint recognition can be divided into contact mode, contactless mode and mobile mode. Mobile mode is a special case of contactless mode, which can be considered as the most difficult contactless mode. The preprocessing on contact mode is easier than those on the other two modes. Table 1 summarizes the palmprint preprocessing methods in contactless mode.
| Reference | Background | Segmentation | Description |
|---|---|---|---|
| [6] | It possibly fails in complex background. | ||
| [7] | Controllable | Skin color model | The uniformity of the intra-class features is poor, and it is unsuitable for complex backgrounds. |
| [8,9] | It possibly fails in complex background. | ||
| [10,11] | Shape model | The computational complexity is high. | |
| [12] | Users’ freedom is low, and the uniformity of the intra-class features is poor. | ||
| [13] | Complex | Assisted | The assisted techniques are complicated, which degrades the comfortability. |
| [14] | DLSP reduces the localization error and computation complexity, but the invalid area is large. | ||
| [15] | Improved active shape model | The computational complexity is high. |
Palmprint recognition methods can be briefly divided into five categories [16], namely coding-based methods, structure-based methods, subspace-based methods [17], statistics-based methods [18], deep-learning/machine-learning based methods. Fusion technologies are also been used in palmprint recognition [19,20]. Because coding-based methods can be free from training and have low storage and computational complexity, they are suitable for edge computing devices such as mobile phones with low-performance hardware. Therefore, coding-based methods, including PalmCode [21], OrdinalCode[22], FusionCode[23], CompCode[24], RLOC[25], BOCV[26], E-BOCV[27], DCC[28], DRCC[28], DOC[29], are employed in our VPR system.
III. METHODOLOGY
The key frame selection in VPR system is shown as in Figure 1. The valid frames, in which users place their hands correctly, are first selected according to finger gap judgement, and then the key frames, which have good quality, are selected from the valid frames according to quality judgement. Some key frames at registration are used as the gallery samples; while each key frame at authentication is used as a query sample and matched with the gallery samples until the authentication request is approved.
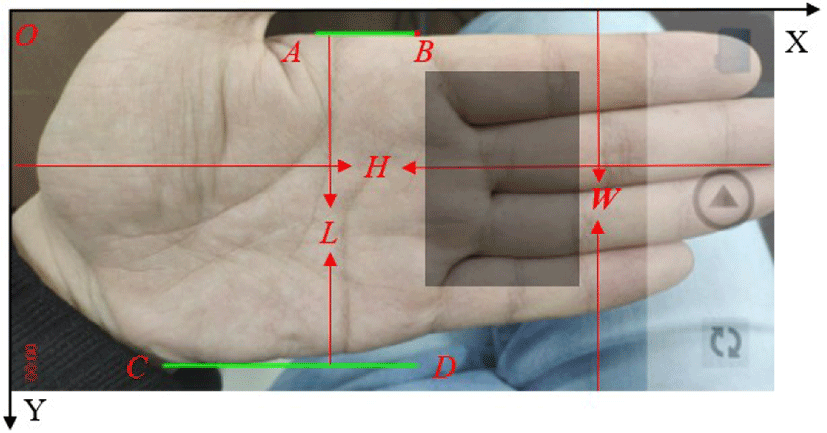
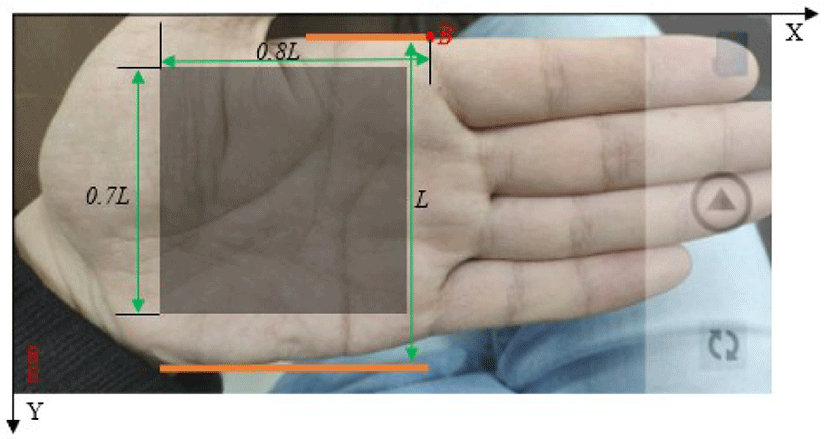
DLSP assisted placement technique can overcome the challenges as well as effectively reduce the localization error and computation complexity. However, the assisted lines in DLSP are oblique, so there are large invalid area. In addition, the preprocessing is not easy conducted along oblique directions. Thus MDLSP technique is developed to reduce the invalid area in the frames and facilitate computation. Figure 2 shows the assisted placement interface for left hand in VPR system. The interface can be mirror flipped for right hand. The invalid area is very small, and the computation can be easily conducted along horizontal and vertical directions.
In MDLSP, there are two horizontal assisted lines (long line CD, short line AB) and one assisted point B (the right end point of line segment AB) on the screen. The point O in the upper left corner is the origin of the coordinate system. The positive directions of the X-axis and Y-axis are horizontally rightward and vertically downward, respectively. The positions of the assisted graphics are defined as follows.
The image is a horizontal screen preview on mobile devices. The width and height are W and H, respectively. When the palm surface is parallel to the interface surface, the upper and lower boundaries of the palm are approximately parallel to AB and CD, respectively. Let the two end points of the upper boundary be A(xA, yA) and B(xB, yB), respectively.
Let the two end points of the lower boundary be C(xC, yC), D(xD, yD).
The distance between line segment AB and CD is L.
L determines the distance from the palm surface to the camera. A user needs to keep his/her palm surface and the lens at a proper distance.
A user should place his/her hand according to the following rules.
-
The four fingers (index, middle, ring and little fingers) are naturally brought together, and the thumb is spread out.
-
The upper and lower boundary lines of the palm should be aligned with and tangent to the two assisted lines.
-
Point B should be aligned with the intersection of the upper boundary of the index finger and the bottom line of the index finger.
The valid frames are selected according to the finger gap judgement [14]. The finger gap is the sub-region of hand, i.e., the shaded rectangle in Figure 2. The location of shaded rectangle is:
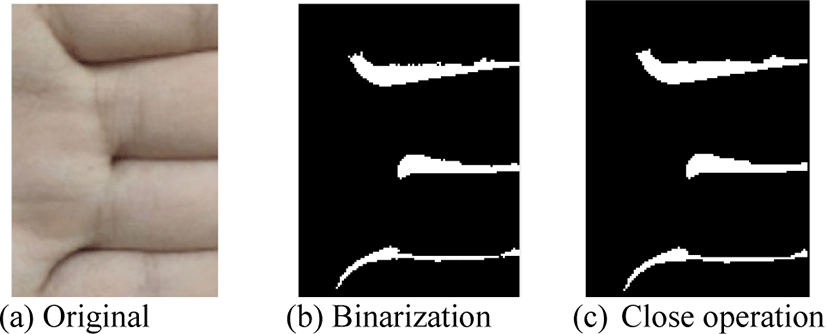
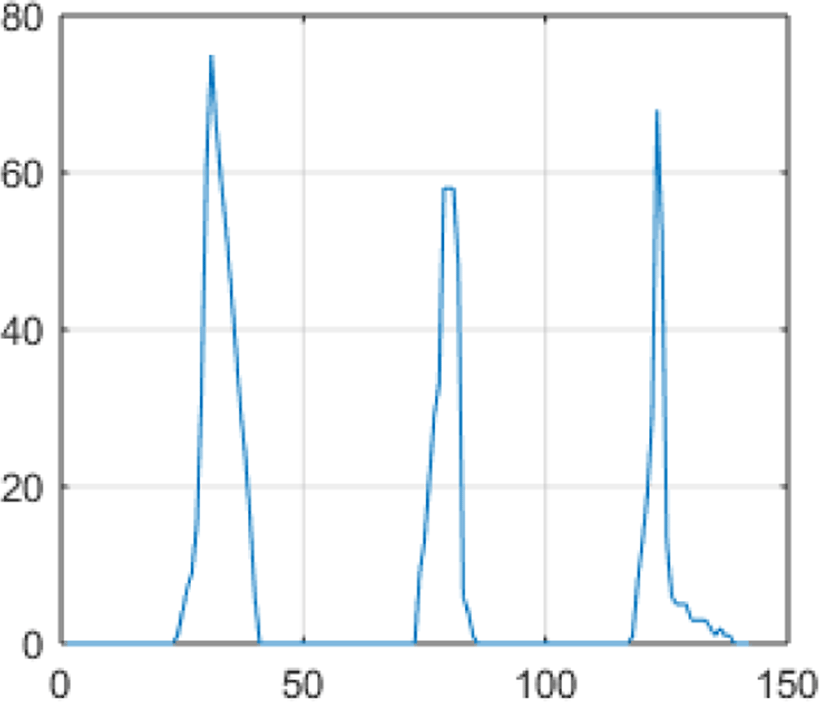
If the dark rectangle has the finger gap, i.e., the finger gap appears at the correct location in one frame, which demonstrates that the user places his/her hand correctly according to the assisted placement, then this frame is considered as the valid frame. The finger gap processing is shown in Figure 3 and its horizontal integral projection is shown in Figure 4.
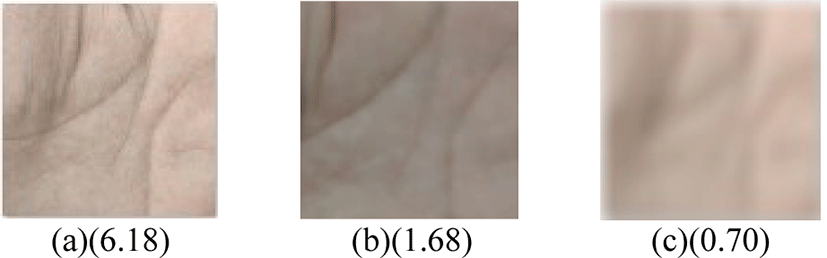
For the image evaluation without reference, the gray-scale variance product is used to evaluate the quality of valid frames, which is defined as:
In order to reduce the computation complexity, only the quality of ROI is evaluated. Valid frames have different qualities, as shown in Figure 6. The valid frames, whose gray variance products are higher than β, are selected as the key frames.
The system inputs the gallery video, and the ROI set is Rr={r1, r2, …, rn-1, rn}. The template set generated from ROI set is Tr={t1, t2, …, tn-1, tn}. Assume that the number of gallery templates is k, the registration distance judgment threshold is hr, and the gallery template set is , the gallery templates are generated by the following registration algorithm.
Registration algorithm
Input: The number of registered templates, k, the registration distance judgment threshold, hr, the template set Tr is generated from the ROIs cropped from the gallery video frames, Tr={t1, t2, ..., tn-1, tn}.
Output: Gallery template set , or registration failed.
p=0;
fori=2; i<=n; i++ do
d=Hamming distance(ti-1, ti);
ifd<h
p++;
ti add to Tr’;
else
p=0; clear Tr’;
ifp>=k
break;
elsecontinue;
end for
if length(Tr’)==k
returnTr’;
else registration failed;
During authentication, the system inputs the authentication video, and the template set of the ROI is Tv={t1, t2, …, tn-1, tn}, the authentication distance threshold is hv, then the authentication algorithm is:
Verification algorithm
Input: The query template set Tv={t1, t2, …, tn-1, tn} is generated from the ROIs cropped from the query video frames, gallery template set , authentication distance threshold hv.
Output: authentication succeeded or failed.
fori=1; i<=n; i++ do
forj=1; j<=length(Tr’); j++ do
ifd<hv
return authentication succeeded;
else continue;
end for
ifi>n
return authentication failed;
end for
IV. EXPERIMENTAL RESULTS
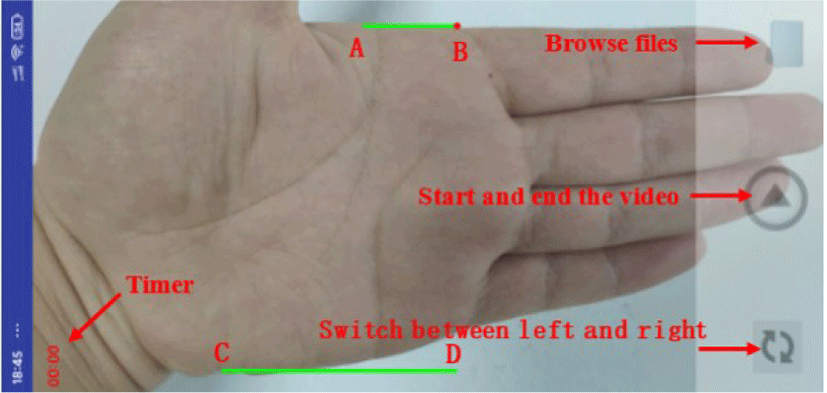
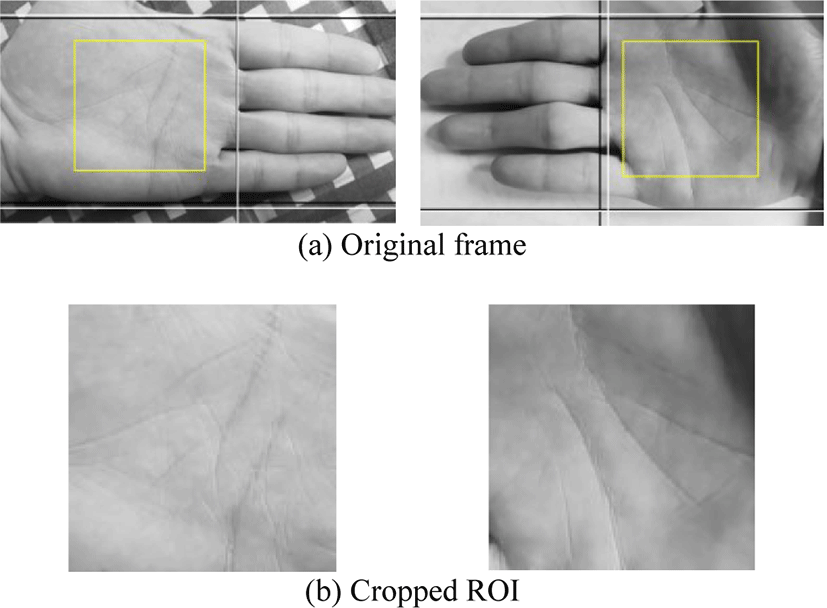
The hand video capture application is shown in Figure 7. We capture totally the videos of 100 left and right hands of 50 persons, each palm has 5 videos. Each video lasts about 6 seconds and its size is about 10MB. The ROIs are cropped from valid frames, as shown in Figure 8.
Equal error rate (EER) and decidability index d’ are used to evaluate the accuracy. d’ is defined as:
where μ1 and μ2 are the mathematical expectations of intra-class and inter-class normalized Hamming distances, respectively. σ1 and σ2 are the standard deviations of intra-class and inter-class normalized Hamming distances, respectively.
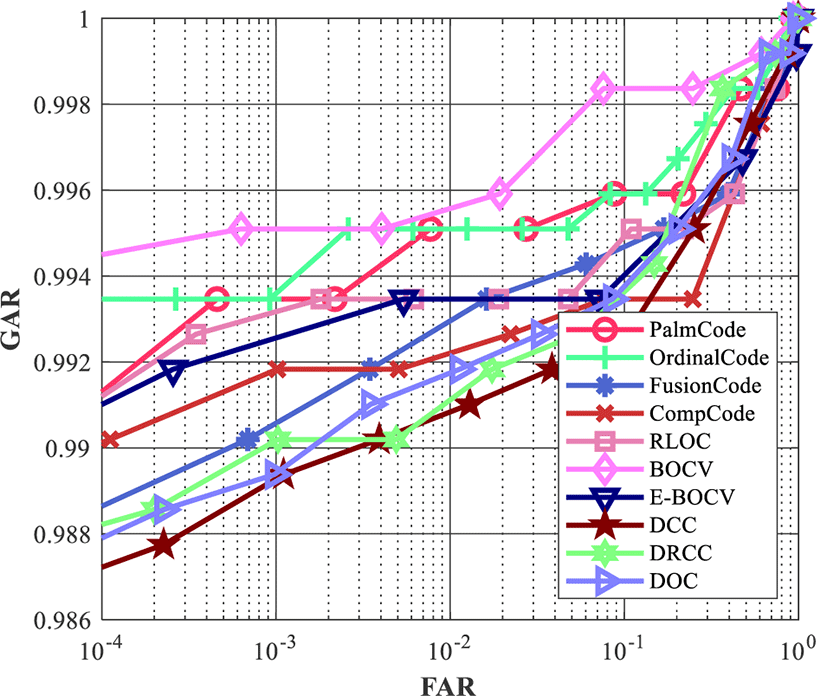
Table 2 shows the EER and d’. Figure 9 shows the ROC curves. The experimental results demonstrate the effectiveness of our VPR algorithm and system.
V. CONCLUSIONS AND FUTURE WORKS
Palmprint recognition in video media is a novel technology. This paper modifies DLSP technique to reduce the invalid area in the frames. In addition, the valid frames are selected according to finger gap judgement, and then some key frames are selected from the valid frames according to image quality as the gallery samples that are matched with the query samples for authentication decision. The VPR algorithm is conducted on the system designed and developed on mobile device. In future, we will further modify the assisted technique or develop other state-of-the-art assisted techniques, and employ other recognition methods, such as deep learning, to improve accuracy.