I. INTRODUCTION
With the progress of IoT, in the near future, all hardware devices in the world will be networked [1]. IoT is a huge network composed of computer equipment and hardware equipment connected to the Internet. Over the years, people's lives have undergone earth shaking changes with the application and development of IoT, specifically in making work and life more convenient [2]. It is widely used in daily life. In terms of home furnishing, smart home can enable individual users to remotely control the working state of home appliances, provide individuals with an intelligent life mode, and help people effectively arrange time and save energy [3]. In medical treatment, people can install node sensors on patients to monitor the indexes of patients' bodies. When the indexes are abnormal, people can automatically call for help; In terms of traffic, communication between vehicles and roadside units can enable vehicles and roadside units to grasp the driving conditions of other vehicles in time, adjust their driving conditions in time, and achieve the purpose of optimizing traffic conditions. Internet of Things realizes the intelligence and automation of the system through the inter-connection between sensors and controllers. The application of related technologies lays a good foundation for the popularization of IoT. In addition to the above functions, IoT has been widely used in agriculture, medical care, energy, Internet of Vehicles and other fields, playing an indispensable role in urban intelligence. In the common Internet of Things, there are generally two types of entities. They are sensor nodes and server nodes. Sensor nodes collect data and execute the received instructions. Server node uploads the data and sends instructions, and performs a series of operations. Whether users are in the system deployment range or far away, they can control by sending instructions to nodes after completing identity authentication [4].
The Internet of Things technology is developing rapidly, but its security issues have also attracted widespread attention. So far, there is no unified industry standard for the Internet of Things industry, and a large number of IoT devices and systems in the market have security risks [5]. Although the Internet of Things has brought great convenience to our lives, once its security vulnerabilities are exploited by criminals, the losses to individuals, industries, and even the entire society are enormous. The Internet of Things has its own unique architecture, and what sets it apart from the general Internet is the perception layer. Combining the unique security threats of the Internet of Things, it can be seen that the biggest issue with Internet of Things security is also the perception layer security. The IoT perception layer is generally used to collect data required by servers to achieve fixed functions and transmit it after simple processing. The perception layer mainly consists of various terminal devices, such as sensors, gateways, RFID readers, intelligent terminal devices, etc. The first step in realizing the functionality of the Internet of Things network is to use these terminal devices to collect data, so the perception layer is also the foundation of the Internet of Things [6]. Without the work of these devices, the Internet of Things cannot be discussed. However, in the general Internet of Things, the number of terminal devices is huge, and in practical applications, it does not require too much manpower and resources to supervise them. Therefore, from a physical level, its security management is weak. At the communication level, these devices are also very susceptible to various attacks such as impersonation, interception, Distributed Denial of Service (DDoS), replay, etc. Due to the lack of identity verification on terminal devices, the vast majority of IoT devices operate in a white box environment, resulting in extremely fragile security around the IoT [7]. Attackers use these issues to continuously launch attacks on IoT devices, and once successful, it will cause huge losses to businesses and even society. Therefore, solving the authentication and communication security issues of terminal devices is a key step in achieving IoT security [8].
While IoT facilitates People's Daily life, its security has not been paid enough attention to for a long time. Now, after being threatened by all aspects and suffering heavy losses, people pay more and more attention to the security of IoT [9]. Compared with traditional Internet, the security of IoT has certain similarities. The protection elements of the Internet of things are still usability and confidentiality. As the increasing scale of terminal access devices and data, some criminals launch malicious attacks by finding, utilizing or controlling Internet of things devices with security vulnerabilities [10]. Therefore, security issues are not only related to the interests of users, but also have a great impact on economic development, social stability and national security [11]. Here, we need to use cryptographic theory and technology to build a scheme to provide a comprehensive security mechanism. However, in the environment of IoT, a large number of devices are constrained [12]. Due to their own limitations, their computing power and storage capacity are relatively limited, and they are very vulnerable to enemy attacks [13]. In order to provide appropriate security protection for these restricted devices, we need to design appropriate security schemes to encrypt their privacy and provide verification for transmitted information based on the authentication of both sides of the communication, so as to resist various types of attacks. Therefore, we propose a secure authentication protocol for IoT, which is based on chaotic mapping algorithm. In the interaction, the communication entities need to authenticate and negotiate the key, through which they can communicate securely. The main contributions are arranged as follows:
-
In view of the problem that the authentication process of Internet of things devices divulges users’ privacy, a lightweight device identity authentication protocol is proposed by using chaotic mapping algorithm technology. This scheme provides device anonymity protection and secure negotiation of session key to ensure the subsequent secure communication.
-
It is proved by BAN logic Scyther and informal security analysis that the protocol satisfies anonymity, and realizes mutual authentication and secure session key negotiation.
-
Through the experiment, the protocol can not only ensure the security of identity authentication, but also has less overhead compared with other protocols.
The rest of this paper is structured as follows. Sections 2 and 3 mainly focus on relevant research and preliminaries. Section 4 is about the details of the protocol we propose. Section 5 mainly verifies the security of the protocol. Section 6 mainly analyzes the protocol. Section 7 summarizes the whole paper.
II. LITERATURE REVIEW
Recently, some researchers have conducted extensive research on user identity authentication schemes in the Internet of things.
Sahingoz et al. [13] proposed a multi-level dynamic key agreement protocol, which was based on asymmetric key negotiation and ECC password. In the protocol, each device negotiates with adjacent nodes to complete the verification and signature of data, which increased the amount of calculation, leaded to serious energy loss of nodes, and shortened the service life of nodes. Liao and Hsiao proposed a security authentication scheme based on elliptic curve [15], which integrated the identity authentication server, but Peeters and Hermans [16] pointed out that it was vulnerable to server simulation attacks. Kalra and Sood [17] pointed out in their paper that the embedded devices in IoT and cloud server cannot support complex encryption algorithms and had limited storage capacity. To solve the above problems, using elliptic curve cryptography, they designed a scheme for two-way authentication and key negotiation between Internet of things devices and cloud server. This scheme used cookies to realize the authentication of identity legitimacy of intelligent devices. However, Chang et al. [18] proved that Kalra's scheme had two security defects, that is, it did not realize the mutual authentication, and the key was fuzzy. They improved the original scheme and proposed a more complete and secure improvement scheme. The server verified the legitimacy of the server to the device by generating secret values for the device in the device registration stage, Using elliptic curve to realize key negotiation solved the problem of session key ambiguity. Liao and Wang [19] proposed a shared key protocol. Because there are many servers that provide services for users, identity authentication schemes needed authentication protocols applied to multi server environments. Vaidya et al. proposed a device authentication mechanism in smart home environment, which can meet known security features such as forward security and key leakage attacks, but the security of this mechanism had not been demonstrated in the paper [20]. Li designed a secure authentication protocol in the Internet of things environment, which used packet monitoring and a control record to simplify the authenticat ion process, and can establish session keys between communication entities [21]. However, the protocol cannot resist simulation attacks, and realize the anonymity of user identity. Han et al. proposed a secure authentication protocol in smart home system, which realized two-way authentication between smart devices and gateways [22]. However, for devices with limited resources, the protocol required large overhead. Fabian et al. designed a distributed hash table to realize the anonymity of intelligent devices and prevent privacy disclosure [23]. Chaudhry et al. [24] proposed an authentication protocol based on ECC. The protocol completed the identity authentication process through exchanging two messages. Abbasinezhad-Mood and Nikooghadam [25] proposed an anonymous self-authenticated key distribution protocol based on elliptic curve cryptography. Kim et al. proposed a dynamic and effective authentication scheme in the Internet of things environment, which realized the dynamic selection of authentication policy and reduced the computational cost of the protocol [26]. However, the protocol still cannot realize the anonymity of user identity and the non connection between users. Medaglia and Serbanati [28] listed and explained the problems faced by user privacy protection and encrypted communication in the Internet of Things, and gave improvement suggestions for the listed problems from the perspective of short term and long term respectively. The technologies in the shortterm plan were mostly existing or under study, while those in the long-term plan remained in the conceptual stage temporarily. Fernandes et al. [29] directly conducted a series of tests and analyses on SmartThings, Samsung's smart home application system. In addition, other experts have analyzed and summarized the security environment of different specific application environments [30]. Vaidya et al. [31] proposed a password-based remote user authentication protocol, but their protocol did not provide twoway authentication between entities, and the scheme was vulnerable to smart card theft attacks. Wazid et al. [32] proposed a multi-factor user remote authentication and key negotiation protocol, which introduced a tool called biological key. Users needed to provide passwords and personal biological templates at the same time to complete identity authentication, and regarded the gateway node as a secure device that could not be stolen, which was somewhat different from the actual application. Kumar et al. [33] designed a secure key protocol suitable for smart home. This protocol can provide mutual authentication between two communication parties and establish temporary communication keys. However, this protocol only gave a general framework.
III. PRELIMINARIES
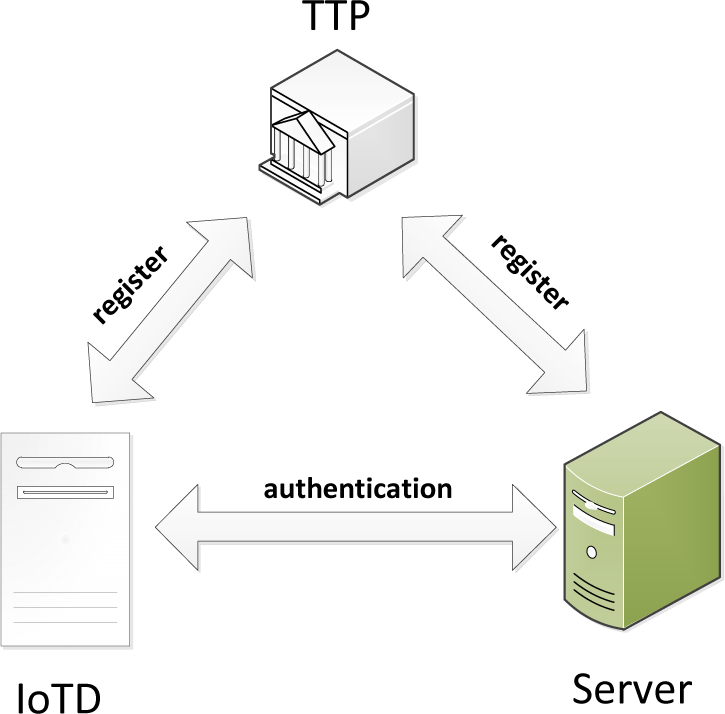
As shown in Fig. 1, the protocol authentication system model is mainly composed of the following entities: Trusted third parties (TTP), Server and IoT devices (IoTD). TTP has enough computing and interaction capabilities to complete any complex task. In this agreement, TTP mainly generates the public parameters, the keys of IoTD and Server, and It can be trusted. Server can verify the information sent by IoTD and negotiate a session key. IoTD is the device that can provide some services, which can be various types of sensors, and need to reach mutual authentication with the server.
This paper will adopt the universally considered threat model in the IoT security threat model [11]. Like most authentication schemes, this paper first considers the Dolev-Yao threat model [27]. In this threat model, the participants in the key agreement scheme communicate on insecure channels. Opponents can eavesdrop on all messages in communication and modify or delete them after interception. Opponents can send modified or directly forged information to participants in order to obtain favorable returns. Opponents can shape themselves as legitimate participants in key negotiation and actively attempt to participate in session key negotiation.
Due to its own characteristics, the Internet of things faces a variety of attacks, so the design of Internet of things authentication scheme faces many challenges. Generally, a relatively perfect IoT authentication mechanism should have these attributes [8].
-
Mutual authentication. The authentication scheme must meet the requirements that two entities in the communication can mutually verify the legitimacy of each other's identities.
-
User anonymity. Because communication in an open environment, the attacker may track the activities of legitimate personnel to steal the identity of the device. Therefore, the designed authentication scheme of the Internet of things should protect the secret identity information of the device and provide anonymity
-
Forward security. An attacker may acquire the longterm key and use it to try to retrieve key. Therefore, it is necessary to ensure that even if the key is leaked, it will not lead to the session key leakage of historical communication.
-
Anti-attack. Anti-attack requires that the protocol can resist common network attacks such as replay attack, counterfeiting attack, etc.
-
Availability. A reasonable security authentication scheme should have the characteristics of energy saving. The scheme design should avoid complex computing as much as possible, reduce computing overhead and communication consumption, so that it can be truly applied in the Internet of things with limited resources.
-
Security key update: The session key is used to ensure data security and needs to be updated after each data transmission session. In addition, it is also necessary to properly manage the security keys to achieve key synchronization between both parties.
-
Data confidentiality and integrity: The transmitted data needs confidentiality protection and integrity protection.
Hash function is a class function that can map data of different lengths to fixed length data. The output fixed length data is called hash value. Because hash function is sensitive, minor changes to the original data will lead to huge changes in its hash value. It can be regarded as the only fingerprint of the original data, and it has an irreversible nature. Therefore, hash function is usually used to ensure the integrity of data and conduct authentication. A good hash function should have the following characteristics.
-
Fixed length. This is the basic property of the hash function, that is, it can convert an input of a certain length into a hash of a fixed length. In most cases, the input length is greater than the output length.
-
Pseudorandomness. If the hash function does not have good pseudo randomness, the probability of collision will increase, which will lead to some hash values being more likely to appear than other hash values, and the cost of handling collisions will increase. Therefore, a good hash function should have good pseudorandomness.
-
Easy to calculate. This is easy to ignore, but only when the hash function is fast enough can the efficiency of encryption and other operations be guaranteed.
-
Collision resistance. The most ideal hash function is completely collision free, that is, any hash value has only one input corresponding to it. But in general, considering the actual application scenarios, we only need a hash function with minimal collision probability.
Generally, the algorithms corresponding to hash function are public. This property also makes hash function popular in many fields, but attacks against different hash function also occur. The current attack against the hash function is mainly a hash collision attack, which is essentially a denial of service attack. This attack is aimed at constructing data according to the characteristics of the hash function, so that through the calculation of the hash function, all data have the same hash value. When these data are saved in the hash table, the hash table will become a single linked table due to a large number of collisions, Thus, the time complexity of various operations on the hash table is greatly increased to achieve the goal of preventing the system from responding quickly.
Given an integer n and a real number x with a value in the range of [−1,1], we define the Chebyshev polynomial as a mapping such as Tn: [−1, 1]→[−1, 1], where: Tn(x) = cos(narccos(x)). The polynomial recursive relationship between different orders is defined as: . In addition, it also has the properties [11].
Zhang extended this property to the real number field (−∞,+∞): Tn(x)=(2xTn−1(x)−Tn−2(x)) mod p where when , p is a large prime number, the Chebyshev polynomial still satisfies this property .
IV. THE PROPOSED SCHEME
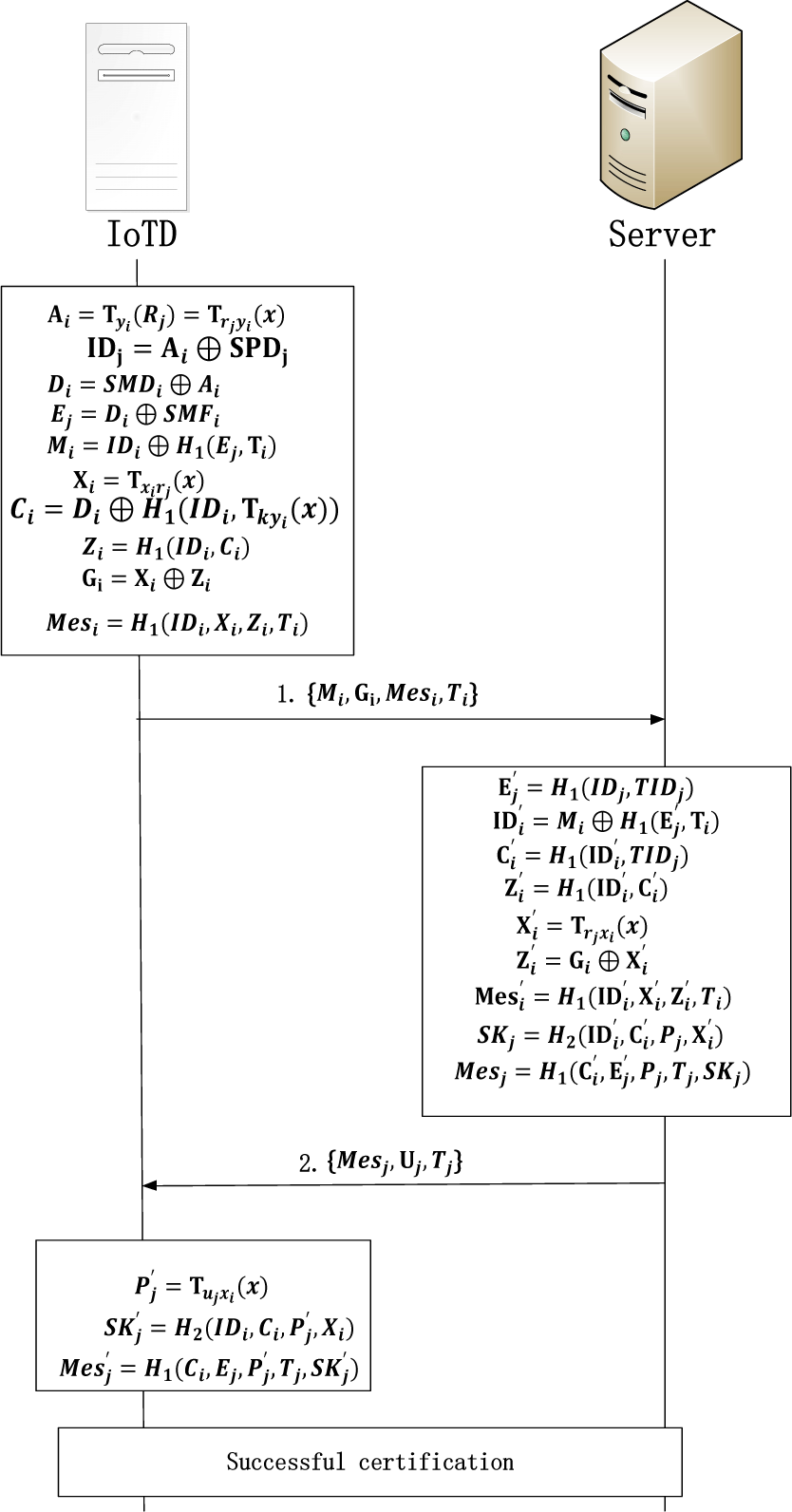
The design details of the authentication protocol will be described, and the symbols and their meanings used will be introduced. Here, The specific symbols and their meanings are shown in Table 1, and the specific protocol flow is shown in Fig. 2.
TTP selects two integers randomly x and k and P is a large prime number selected by TTP. TTP calculates TK = Tk (x) mod P, where k is the secret private key. TTP selects two secure hash functions: H1 :{0,1}*×{0,1}*→Z*q, . Finally, TTP releases the system parameters {x,Tk(x),P, H1,H2}.
First, the server Sj randomly selects a secret value and the real identity IDj. Then it sends the message to TTP securely. When the TTP gets this information, it needs to be verified whether the identity has been registered. If you have already registered, refuse to register, otherwise continue. Then TTP calculates the , stores in the database, and sends the message to Sj. Sj stores the to the database.
-
IoTDi first selects the identity information IDi and randomly selects , calculates , and sends to TTP securely.
-
When getting the message, TTP will query whether the identity exists. If this identity already exists, it indicates that it has been registered, and the request is rejected, otherwise continue. TTP calculates , , . Then TTP sends to IoTDi through secure channel.
-
IoTDi calculates , , , and finally stores the value into memory.
When IoTDi and Sj communicate, IoTDi and Sj need to authenticate and establish a session key.
-
IoTDi first calculates then , , , . Next, IoTDi generates the current timestamp Ti and calculates . IoTDi selects a new secret value and calculates , , . Finally, IoTDi sends message to Sj.
-
When Sj receives the information, Sj checks the correctness of the timestamp Ti. If it is not legal, it refuses to authenticate. Otherwise, it calculates , , , , , and then checks whether the values of and Mesi. If their values are the same IoTDi is authenticated. Then, Si generates a secret random number and timestamp Tj, calculates , and session key , and then sends the message to IoTDi
-
When IoTDi receives the information from Sj, IoTDi checks the correctness of the timestamp Tj. If it is not, it will refuse authentication. Otherwise, IoTDi calculates , , and verifies whether the messages and are the same. If two values are the same, IoTDi verifies Sj and the generated session key are also equal. At this time, IoTDi and Sj can communicate through the session key.
V. SECURITY EVALUATION
BAN logic is a modal logic based on agent knowledge and belief reasoning [11]. In this logic, a series of artificial symbols are specified to form a formal marking method to describe protocol messages, protocol assumptions, inference rules and subject beliefs. BAN logic, under the action of axioms and inference rules, derives the subject's belief from protocol assumptions and protocol messages to judge whether the protocol meets the set goal. This section describes the use of BAN logic to verify the security.The logic rules are shown in Table 1.
The following describes the specific steps:
-
1) Idealized form of protocol
-
2) Protocol goal
-
3) Protocol initialization assumptions
-
4) Proof of protocol
From M1, we can get:
From R1, A1 and message meaning rules, we get:
From R2, A2 and nonce number verification rules, we get:
From R3, A3 and jurisdiction rules, we get:
From R4, R2, A4, A5 and , we get:
According to R5, A6 and jurisdiction rules, we get:
From the message M2, we can get:
Through R7, A5 and message freshness rules, we get:
From R7, R7 and message meaning rule, we get:
From R8 and random number verification rules, we get:
Through R10, A7, A8, A9 and , we can get
According to R11, A10 and jurisdiction rules, we get:
Through R5, R6, R11and R12, we can see that our protocol has reached the goals.
Scyther is widely used to verify protocol security [27]. The formal verification tool Scyther is an effective tool developed by C. Cremers based on model improvement algorithm and widely used to verify security protocols. The Scyther tool can effectively verify and analyze security protocols by characterizing protocols and generating limited representations of all possible protocol behaviors, and by detecting unlimited number of sessions, random numbers, and potential attacks and vulnerabilities of specific statements. At the same time, the tool can give explicit termination to protocols of unlimited sessions and infinite state sets. Because Scyther tool has a clear description, it can effectively help the protocol to conduct attack search. Scyther assumes that all encryption functions are perfect, that is, plaintext messages cannot be decrypted without knowing the key. The tool transforms the unlimited behavior space of the protocol into the limited output of the protocol.
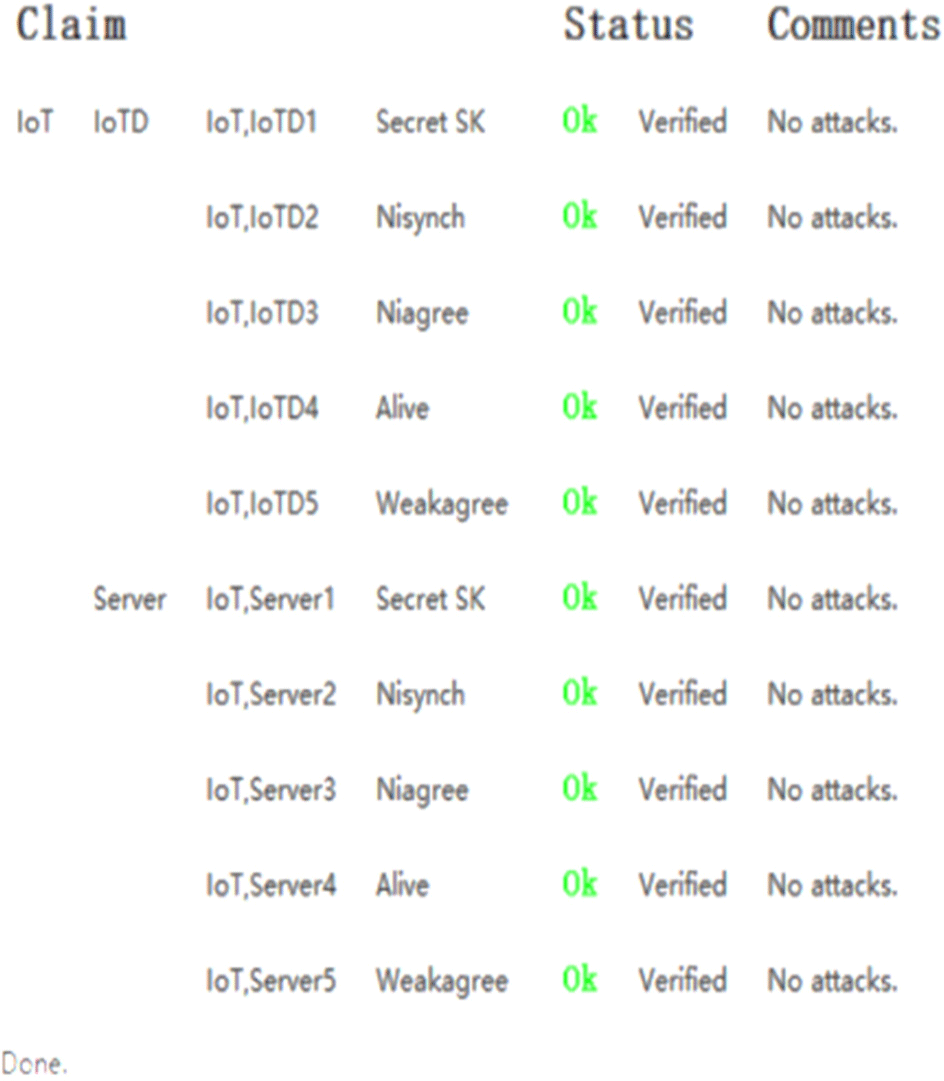
In this paper, the formal analysis tool Scyther is used to formally analyze the proposed protocol. In the protocol, there are mainly two roles IoTD and Server. Scyther models the protocol and analyzes it using security statements. And the article explains different verification levels through the statements, including alive, weakagree, niagree, and nisynch. Alive and weakagree can resist MitM attack. Niagree and nisynch can resist replay attack and ensure forward and backward security.
The operation results after scyther analysis are shown in Fig. 3. From the analysis results, it can be concluded that This protocol satisfies the security requirements in IoT.
Here, we analyze the security attributes.
-
Mutual Authentication. The scheme can realize mutual authentication between Sj and IoTDi. IoTDi generates secret values Mesj = H1(IDi,Xi,Zi,Ti,) and sends them to Sj, which verifies their correctness and authenticates IoTDi. Sj generates through secret value and sends it to IoTDi. IoTDi) verifies its correctness and authenticates Sj.
-
Anonymity. The scheme provides privacy identity protection of IoTD_(i) identity. In our scheme, IoTDi generates a temporary identity . Because the timestamp generated by each authentication is different, the temporary identity of the device is different every time. And it is encrypted. Only the legal Sj can decrypt the real identity of IoTDi.
-
Session Key Agreement. In the scheme, IoTDi and Sjnegotiate the session key through the chaotic mapping algorithm
-
Resist replay attack. The transmitted message {Mi,Gi,Mesi,Ti } and {Mesj,Uj,Tj} in the scheme contain a new timestamp and random number. If the receiver receives the corresponding message, it first verifies it to ensure that its message is fresh. Thus, the attack can be prevented.
-
Resistance to MitM attack. Both IoTDi and Sj generate corresponding messages with message veryfication information, so IoTDi and Sj) will check the legal of the corresponding information when they receive them, which can effectively resist the attack.
-
Resistance to counterfeiting attacks. IoTDi and Sj) in the scheme are the effective information generated by their respective secret values, so the attacker cannot construct a legitimate message if he does not know the corresponding secret values, so the scheme can effectively resist counterfeiting attacks.
-
Forward security. IoTDi and Sj in the scheme calculate Pj =Tujxi (x) and to generate SK. And even if SK is leaked, SK negotiated in the next authentication process can be deduced. The forward security of the key is guaranteed.
-
Security key update. IoTD generates a new secret value xi, generates a secret value through a chaotic mapping algorithm, and then generates a session key Server generates a new secret value uj, generates a secret value Pj =Tujxi (x) through the chaotic mapping algorithm, and then generates , so the session key is secure. Then, when authentication is performed again, IoTD and Server need to regenerate new secret values and generate new secret values through chaotic mapping. Therefore, the session key they generate is different each time, which ensures the update of the session key.
-
Data integrity protection: An attacker can destroy the integrity of message data by intercepting, modifying, or inserting data exchanged by users. In the protocol, we can check the integrity of messages because the messages exchanged use the message authentication codes and .
VI. PERFORMANCE ANALYSIS
The primary performance metric we consider here is computing and communication costs to evaluate the associated performance of the solution.
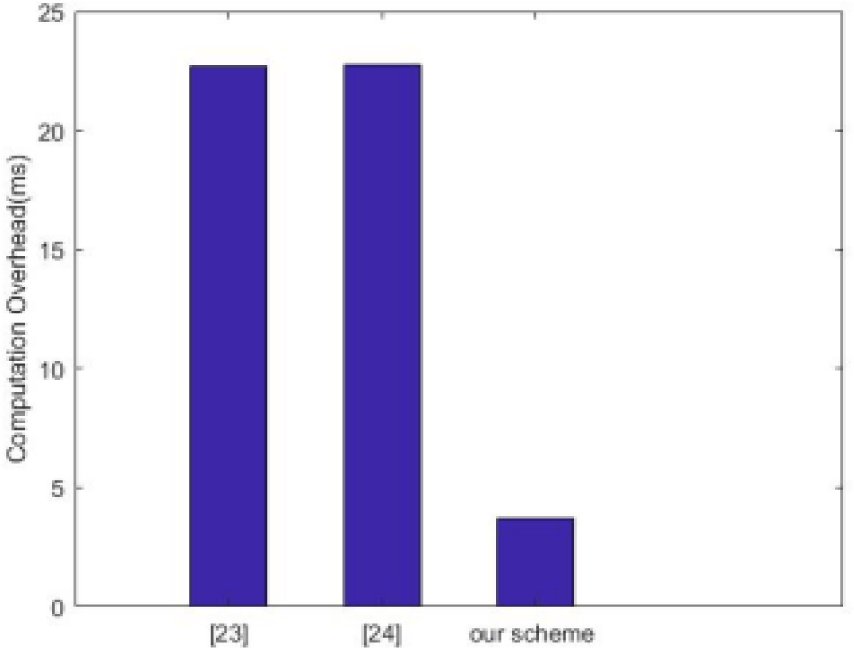
In protocol authentication, computing efficiency is an important indicator of protocol communication performance. If the execution time of the protocol is short, it indicates that the protocol has good communication performance. In this section, two anonymous authentication protocols [23] and [24] are selected to compare with the proposed protocol in terms of implementation efficiency. First, we test the computing time of ECC point multiplication algorithm, ECC point addition algorithm, hash function and chaotic mapping algorithm respectively. Here, the results are TECC=2.46 ms, TECA=0.129 ms, TH=0.04 ms and Tc=0.64 ms. Since the initialization phase and registration phase of the protocol are executed only once, the operation efficiency of the authentication process is the main factor affecting the implementation efficiency of the protocol, so only the computation overhead of authentication process is discussed. In order to verify the calculated cost, we compare them with the scheme, as shown in Table 2 and Fig. 4. From the table and figure, we can see that our scheme has obvious advantages.
| Protocol | Computation overhead | Time |
|---|---|---|
| [23] | 8TH + 9TECC + 2TECA | 22.718 ms |
| [24] | 9TH + 9TECC + 2TECA | 22.758 ms |
| Our scheme | 13TH + 5TC | 3.72 ms |
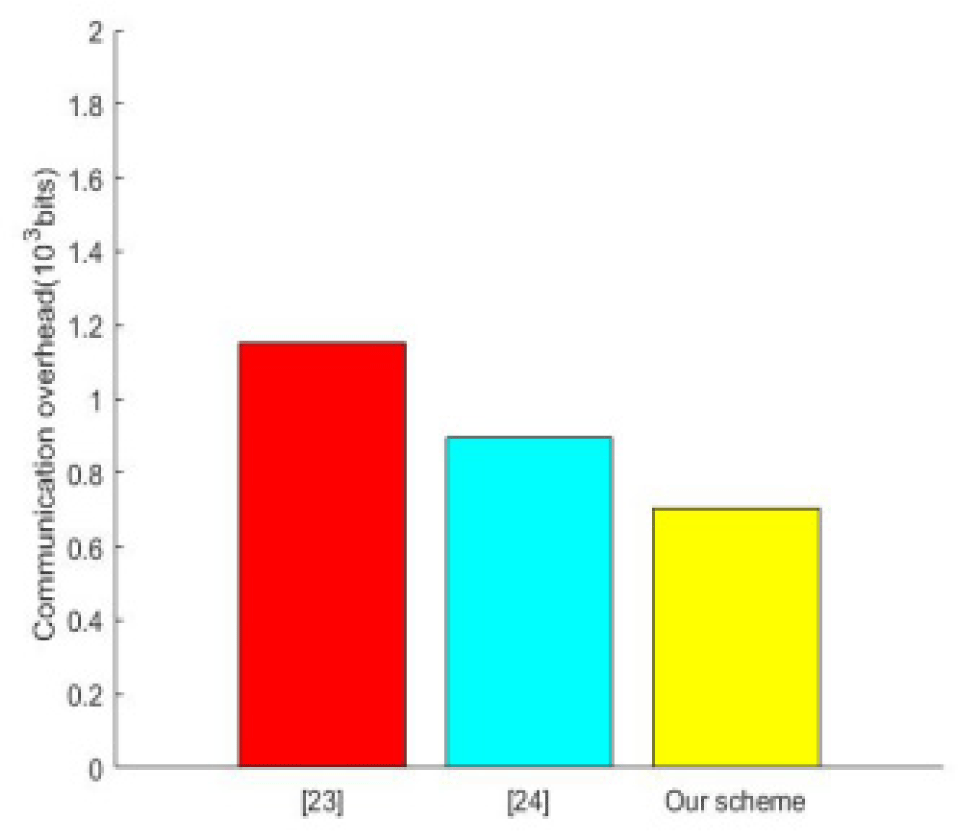
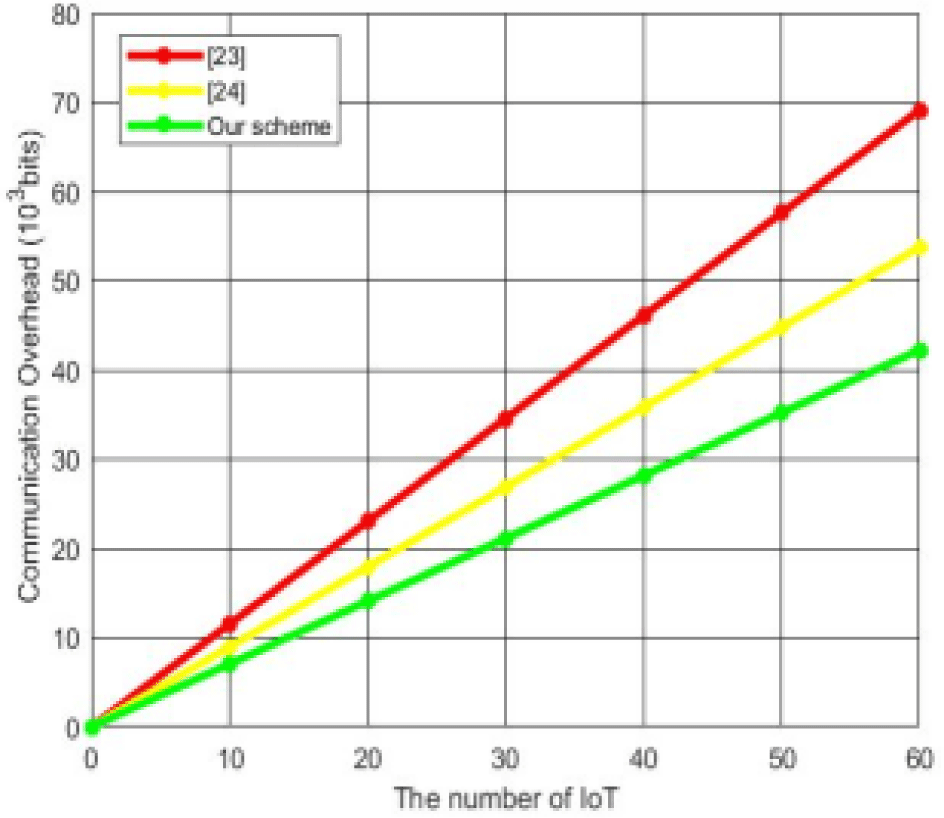
Here we analyze the communication cost of our solution in the authentication stage. We assume that the size of ECC key is 256 bits, the hash function value is 128 bits, the identity information is 64 bits, the timestamp is 32 bits, and the size of chaotic mapping algorithm is 128 bits. In our protocol, IoTD and Server exchange two messages, namely {Mi, Gi, Mesi,Ti} and {Mesj, Uj, Tj}. Through calculation, the communication overhead of {Mi, Gi, Mesi,Ti} is 128+128+128+32=316 bits, and the communication overhead of {Mesj, Uj, Tj} is 128+128+32=288 bits. Therefore, the total communication overhead is 960 bits. The communication overhead of similar schemes [23] and [24] is 1,152 bits and 896 bits respectively. Here we calculate the communication overhead, as shown in Table 3, Fig. 5 and Fig. 6. From the table and figure, we can see that our scheme has obvious advantages.
| Protocol | Communication overhead |
|---|---|
| [23] | 1,152 bits |
| [24] | 896 bits |
| Our scheme | 604 bits |
7. CONCLUSION
IoT is widely used in people's lives, and has been widely used in industrial monitoring, telemedicine, green agriculture, intelligent home and other fields. However, the security threats faced by the IoT have become increasingly prominent. IoT is built on the Internet. The security threats encountered by the IoT include not only the security threats existing in the Internet, but also the specific security threats suffered due to the characteristics of IoT. The access mode of IoT mainly depends on networks and has heterogeneity. The complexity of network composition makes it more vulnerable to network attacks. Therefore, Internet of things communication environment is exposed to various security threats, which may undermine their security. Aiming at the communication security and information integrity of IoT, this paper proposes a security authentication protocol of the Internet of things based on chaotic mapping algorithm. This protocol enables Internet of things devices and server to negotiate the key and communicate securely after mutual authentication. The protocol is proved by using BAN logic, Scyther and informal security analysis, and it can resist various security attacks. Finally, our protocol has less overhead.