I. INTRODUCTION
Blockchain is being talked about as the next major IT technology. Although there are not many cases of actual use as immature technology, it is widely applied in various industries such as cryptocurrency, finance, and public sectors to increase efficiency and enable new services that did not exist previously [1-3]. Nevertheless, as to the legal implications of the universalization of blockchain technology, it seems that at least not enough analysis has been made in our country. In particular, considering that the core of blockchain is changes in information sharing and processing methods, it seems important to consider how blockchain can be affected, especially from the point of view of privacy, and how the privacy law can be applied to blockchain, but there is not enough discussion in Korea yet. Therefore, this paper will study technologies and improvement measures to protect personal information protection using the desired blokchain by analyzing the meaning and implications of blockchain technologies and their services from the perspective of the Privacy Act I will also deal with the introduction in Chapter 1. Chapter 2 discusses blockchain and personal information protection, while Chapter 3 shows the final conclusions in Chapter 4 of the technologies and services required when blockchain is connected to personal information. This addresses the paper that incorporates blockchain into the required personal information. And personal information protection becomes very important in Europe's GDPR, the US Privacy Act, and Asia's Privacy Act. Due to the leakage of personal information, there is still leakage of personal information using hacking etc. based on cyber attacks using internet weaknesses such as phishing, pharming, and smishing. Therefore, the proposals were made on the basis of Anonymous, Autonomy, Openness, Programmable, Traceability, Tamper Proof, and Collectively Maine, which are characteristics of blockchain to prevent such Internet authentication.
II. Related Research
This paper has various technologies on blockchain, needs for personal information protection, and problems such as GDPR. It also reviews the concept and characteristics of blockchain and deals with specific personal information utilization situations in open blockchain and specific blockchain services in order to provide specific analysis from the perspective of the Privacy Act [4-6].
Blockchain is a ledger management technology based on distributed computing technology where small data under management is stored in a chain-type, link-based distributed data storage environment created based on the P2P method, so that no one can modify it at random and anyone can see the results of the change. This is essentially a form of distributed data storage technology, designed to prevent arbitrary manipulation by operators of distributed nodes as a list of changes that have been continuously changed on all participating nodes. Blockchain technology is used for most cryptocurrency transactions, including bitcoin. Because the transaction process of cryptocurrency is used for de-centralized electronic books, the server runs on each computer of many users running blockchain software, enabling free trade between individuals without central banks [7-9]. Blockchain can be seen as an agreement convergence algorithm that ensures that data on books stored distributed across each node is always available among large nodes. This capability enables the node to run anonymously, or even involve a poorly connected or even untrusted operator. The node of the cryptocurrency has a partial or full blockchain. This eliminates the need to have a centralized database that systems like PayPal need. Whereas the ordinary book records the exchange of checks, receipts, or promissory notes, blockchain is itself a trading book and is a trade certificate [10]. Bitcoin expresses that it exists in the form of unpaid results of transactions. Transactions in blockchain format will be distributed to blockchain networks through software apps such as Bitcoin wallet apps. The nodes in the blockchain network verify the transaction, then add the deal to their books. And the deal spreads the added books to other nodes in the network. These blockchain also suggest a new paradigm in traditional cryptography [Fig. 1].
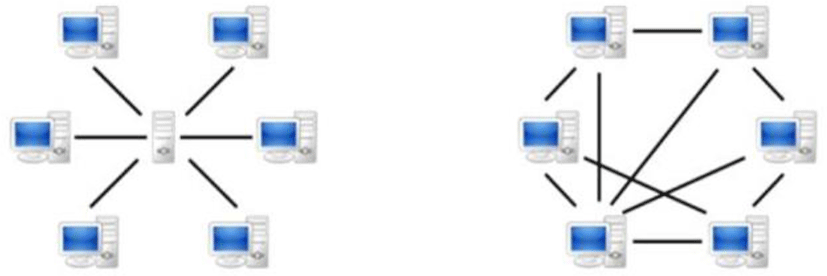
Public blockchain is operated through the Internet and is freely available to anyone without the operator's permission to participate in the blockchain network. Anyone can participate in the network by receiving an address (such as a Bitcoin address) for the transaction and downloading and using software to operate the node. That is, anyone can become a blockchain node, add records to the block, and approve transactions. Because of this feature, it is also called "permissionless blockchain" or "unpermitted blockchain." And in a private blockchain or private blockchain, there is a principal who runs the network, and these entities have the authority to decide whether or not to participate in the network of new participants and the relevant rules [Fig. 2]. This is also referred to as a consotium blockchain. As such authority is granted to one principal or institution, aspects similar to traditional centralized methods are also found, such as rule changes or modifications to existing records. In other words, it is likely that these entities are almost equivalent to TTP (the Privacy Act). Finally, semi-public blockchain (converged blockchain) is a combination of open and private blockchain, in which participation in the network is controlled by a free-flow or some pre-selected participants [11-13].
Information on living individuals, such as names, resident registration numbers, and videos, can be easily combined with other information, even if it is not possible to recognize a particular individual. And personal information is information about identified or identifiable surviving individuals and takes the basic principles of OECD privacy [14-17]. This includes identifying an individual easily combined with other information, even though the information alone does not identify the individual. And the concept and scope of personal information brings about the diversification of the types of personal information that should be protected by continuously expanding information and communication technology development in accordance with the social environment and technology development of technology [Fig. 3].
-
In case there is only a name: As there are people with the same name, the name alone cannot identify a particular individual, so it does not belong to personal information.
-
Statement+Address: Not only the name but also the address can be added to identify a specific individual, so it is appropriate for personal information.
-
Personal identification number: This information is unique and can identify specific individuals, so it is relevant to personal information.
-
Academic background, experience, and degree of property: This information makes an individual assess and judge, so it is relevant to personal information.
III. Analysis of the flow of personal information related to blockchain
In the most circular form of a blockchain, all transaction information associated with such a public key, as well as a party to the transaction, is stored on individual nodes that form a blockchain network in the form of a block. In this case, the information that makes the person identify itself is not stored in the block in principle. In addition, no other centralized server processing unit exists to store and control information. In addition, there is no single entity that makes decisions on important matters concerning processing, such as the purpose and means of processing, and controls them. This is because these decisions are made by consensus algorithms already established in blockchain networks and are implemented at the individual node level. This is the basic picture of an open blockchain, in which anyone can participate in a blockchain network. Thus, people in many countries can be blockchain nodes. This also enables the transmission and exchange of information between countries within blockchain.
Public blockchain is the most faithful blockchain to the basic concept of distributed ledger. As such, it is more like a prototype of a blockchain. As mentioned earlier, the key to blockchain is to process transaction-related information without the presence of a third party, a centralized information processor, and to ensure the reliability of the transaction. And by doing so, the philosophical foundation of blockchain is to ensure anonymity of individuals involved in the transaction and to strengthen their authority over information.The Privacy Act also aims to protect individuals and strengthen their authority.
The Book is in line with these blockchain ideals. In particular, the right to self-determination of personal information, which is the constitutional basis of the nation's Personal Information Protection Act, is defined as "the right of the information subject to decide on its own when and to whom and to which extent the information about itself is known and used, i.e. the right of the information subject to decide on its own regarding the disclosure and use of personal information." In this regard, blockchain and privacy laws share their philosophy [18-22].
On the other hand, however, there is room for thinking that the privacy law does not have a single or specific 'personal information processor' in place of the situation in which blockchain and distributed principal technologies have not been popularized, and that nodes that participate in blockchain networks jointly manage information, and that the system of privacy law does not fit together [23-27].
Public blockchain is the area where potential tension between blockchain technology and privacy laws is most clearly shown. In the case of a private (private) blockchain, only a given node that is allowed to participate by a central administrator on a closed network can handle personal information, which is more consistent with the existing privacy law system that has been passed on to a particular person-handler, but in the case of an open blockchain, an unspecified number of nodes can participate, and no central administrator exists. As mentioned earlier, the most common open block chains are virtual currencies such as bitcoin and ether Leeum. This paper vomits around these open block chains. In this regard, however, attention needs to be paid to the following two points.
The first collection of personal information included in the blockchain for the chain ID service would constitute the collection of personal information. This is done during the process in which users request the issuance of certificates through individual participants. The person who collects the personal information will then be the appropriate participant in the task of issuing the certificate. In addition, the information is automatically shared among each node (participants) in the process of creating a new block containing personal information, which can constitute a third party provision of personal information under the ICT Network Act. The provision of personal information means the transfer of control and control of personal information to third parties other than the personal information processors. In other words, "supplies" include not only the delivery of personal information, but also the sharing of personal information by allowing access to the DB system, allowing access to it, and by enabling copying. In particular, 'supplies' differ from 'personal information processing consignment' in that personal information is transferred for the purpose and benefit of processing the work of the recipient. Participants in the position of the information and communication service provider in relation to the chain ID service shall destroy the information on blockchain when the user has an obligation to exercise the right to delete or destroy personal information in accordance with law by withdrawing their consent to collect and use personal information or to provide personal information to third parties. However, there is a problem with blockchain information that is not easy to delete. The reliability of data in a blockchain is based on indelible immutability, which is cited as an advantage in ensuring the integrity of the data, but the problem is that it is almost impossible to change or delete the data recorded on the blockchain from the perspective of the Privacy Act. as a solution, consider tying all existing data before a particular destruction point into a single block, processing and destroying the hash function. It would not be possible to rule out the possibility that existing data would be treated as permanently deleted in a non-renewable way if the existing blocks were grouped together to disable them and then a new blockchain would be started after the demolition. However, the unclear interpretation of the technical standards and statutes in this part is as discussed earlier.
The principles of data protection should apply to any information concerning an identified or identifiable natural person. Personal data which have undergone pseudonymisation, which could be attributed to a natural person by the use of additional information should be considered to be information on an identifiable natural person. To determine whether a natural person is identifiable, account should be taken of all the means reasonably likely to be used, such as singling out, either by the controller or by another person to identify the natural person directly or indirectly. To ascertain whether means are reasonably likely to be used to identify the natural person, account should be taken of all objective factors, such as the costs of and the amount of time required for identification, taking into consideration the available technology at the time of the processing and technological developments. The principles of data protection should therefore not apply to anonymous information, namely information which does not relate to an identified or identifiable natural person or to personal data rendered anonymous in such a manner that the data subject is not or no longer identifiable. This Regulation does not therefore concern the processing of such anonymous information, including for statistical or research purposes.
As above, the GDPR considers all measures likely to be used reasonably by the controller or another person to determine whether personal information is 'identifiable' but considers all objective factors such as cost, time and available technology. In addition, the expert 26 mentions aliased information 131 and anonymous information, which is described as identifiable information and personal information by the use of additional information, and that anonymous information is not applicable to the Act as information not related to identified or identifiable natural persons. As we saw earlier, within the block, an individual's public key is stored as metadata for transaction information, which seems to be personal information, in that it can be seen as an individual when combined with additional information called a corresponding secret key. As we discussed earlier, the exchange has additional information that enables individual identification, so for the exchange, the information stored within the block may be personal information, but there may be problems with the general node.
IV. CONCLUSION
If the information on the public blockchain can be personal, it may contain the personal information of EU citizens, and some of the nodes may be located within the European Union. Then all the nodes in the European Union can be exploited by the GDPR. Does the node handling the personal information of EU citizens subject to GDPR even if it is not located within the EU? In this respect, the GDPR sets forth explicit provisions for the geographical coverage, unlike our Privacy Act. According to this, nodes within the European Union will be subject to the GDPR once they are in the EU. However, even nodes that are not within the European Union are subject to GDPR if they provide goods or services to information entities within the European Union or monitor the behavior of such information entities within the European Union. First of all, the open blockchain node is responsible for maintaining and managing the transaction ledger so that the blockchain transaction can take place, so this may be considered to be a kind of service provision. However, it should be acknowledged that for GDPR, the fact that the controller is simply not sufficient to provide services to the information entity within the European Union and is clearly expected to provide services to the information entity within the European Union. No literature has been found to have a definitive conclusion on this part. However, this should be assessed on a case-by-case basis, and there is a view that in view of the wider interpretation of Article 3 above, the GDPR is likely to be applied to transactions that are not relevant to the EU. There are numerous difficulties in deciding whether to apply the Personal Information Protection Act to an open block chain and in how the Personal Information Protection Act should be applied. It is thought that a practical solution to such difficulties will be possible only after more social discussions and experience in various use cases of blockchain technology has accumulated to a significant extent.