I. INTRODUCTION
The operation of digital data and its transmission through the network are uncertain operations and are vulnerable to various attacks, cryptography is becoming the most effective means for data security. In the literature, almost all classical methods are still vulnerable to statistical and differential attacks.
This technique, discovered by HILL [1],[2] in 1929, was only applicable to the text. It is based on two main steps. The first step is to divide the message to be encrypted into n character (natural number) blocks, and the second step is in a carefully selected ring as usuallyZ/26ZorZ/256Z) The difficulty of constructing a large invertible matrix prompts researcher to only Use a matrix with n ≥ 4. Equation 1 fully describes this standard technique
With(Ci)is the clear block, is the encrypted block, and (K) is the encryption key. Each (Ci) block is translated to an element of a well selected (Gt) ring. In such a case, the encryption matrix (K) is assigned coefficients in the same ring (Gt). Due to the high degree of linearity, this technique is always exposed to selected plain text and known statistical attacks. On the other hand, the high correlation between adjacent pixels and diagonal pixels of the image makes this technique unsuitable for image encryption. Finally, there is no chain in the encryption system, so this method is vulnerable to differential attacks. The decryption operation is described by next equation.
Several successive developments in the methodology have taken place over time, but all using a reference ring such as (G256) or(G26) which significantly reduces the number of invertible matrixes and increases the risk of brutal attacks.
A first improvement [3-4-5] consists in modifying at each iteration; the encryption matrix by a secret permutation (h) and fixed in the ring (G256) , on the rows or on the columns. This improvement is given by the equation 3
where h (Ki−1) is the transform of the matrix (Ki−1)by fixed permutation (h). Other improvements accompany the static encryption matrix of a translation vector(T) , and this to overcome the problem of uniform blocks [6−7] and null blocks, still others modify the translation vector at each iteration by a linear transformation provided by a fixed matrix (Q) of size (n, n), not necessarily inversible. This method is described by equation 4.
These improvements overcome statistical attacks and selected text attacks, but due to the lack of clear links between the original pixels, encrypted pixels, and encryption keys, they are still vulnerable to differential attacks. However, unless there is a strong correlation between the adjacent pixels of the image and the diagonal, all these methods are still powerless. Recently, the algorithm based on the classic chaotic method has exploded, and the chaotic suite [8−9] has been created to increase the key space, thereby protecting the method from brutal attacks. Unfortunately, due to the difficulty of calculating the inverse of higher-order matrices, these methods still use general non-invertible matrices with n>4 [10],[11], which poses complexity problems. So far, all encryption algorithms have considered the pixel values of the image in ring G256, and the number of invertible matrices of size (n, n) with coefficient G256 is given by the following formula [12], [13].
Faced with the great difficulty of inverting in large-size matrices, the researchers were content to handle matrices of sizes generally less than five, in the classic ring (G256) To correct this anomaly, our contribution provides a convincing solution by treating all pixel values as elements of one of the constructed subjects. Working in the body greatly increases the number of invertible matrices and provides protection. To facilitate algebraic calculations, two chaos tables will be generated.
Moreover, taking advantage of the properties of the involuntary matrices, a new technique for constructing invertible matrices of random size will be determined.
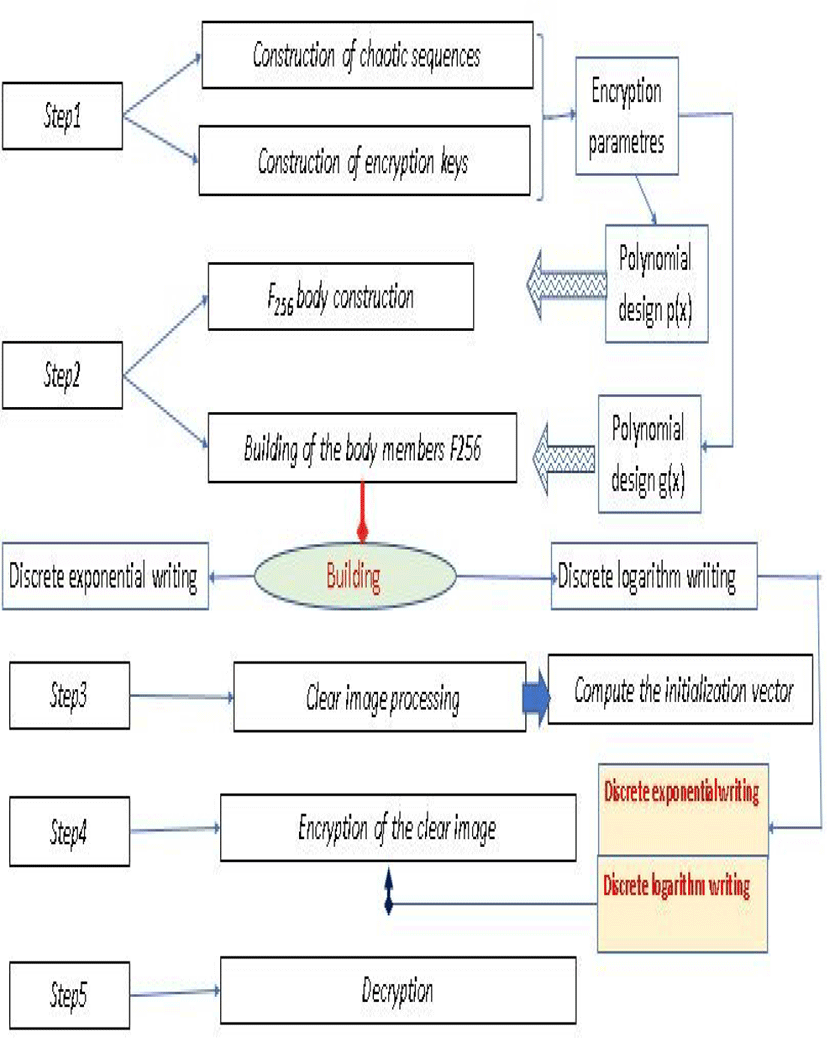
II. THE PROPOSED METHOD
This new technology that works at the pixel level is explained in the following aspects, and its value is regarded as an element of the built company.
Finally, a detailed analysis of our methodology performance will be discussed and compared with other reference systems.
Our algorithm uses two of the most famous and widely used chaotic maps in cryptography.
Due to its high sensitivity to initial conditions, chaos is largely utilized symmetric cryptography for the construction of cipher keys [14],[15],[16].
Henon’s chaotic two-dimensional map was first discovered in 1978. It is described by equation below.
We can convert the two-dimensional map expression to a one-dimensional map that is easy to implement in the encryption system. This formula is described by next equation.
Our work requires the construction of three chaotic vectors(CL), (KR) and (KL) with a coefficient of(G256), and the binary (CR) vector will be regarded as the control vector. This construct is seen by the following algorithm:
We note that
These elements are all non-zero; as a result, they are invertible within the built body.
The most important step is to create an entity with 256 elements, which will replace the classical (G256) in the calculation.
For it
Let
Let p(x) eighth-order polynomial and irreducible in F[x]. We define two internal composition laws described by the following formula on such a set.
It is easy to prove that these two internal composition laws provide the (F256,,⊕; ⊗) with a commutative finite body structure with 256 elements.
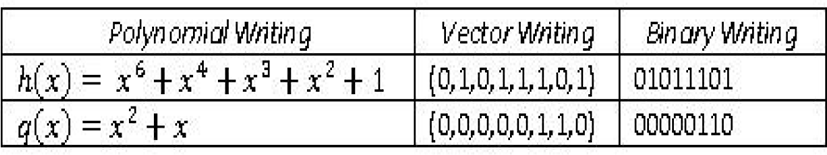
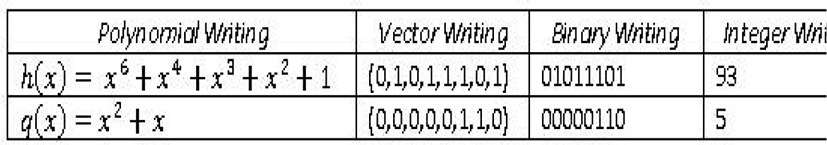
Any element of the F256 body can be represented in five different forms:
We know that
Consequently, any element can be written in the form of a polynomial of degree at most equal to 7 with (G2) components. For example:
Any element of the body F256 can be represented as a size vector (1, 8) with a coefficient in (G2)
By simple conversion from vector writing to binary writing, any element of such a subject can be written in binary form
All body elements are displayed in 8 bits, consequently their value is located between 0 and 255. So, we have
This notation can be extended to the coefficient matrix in F256. For example:
Note that, (F256,, ⊕;⊗) is a finite body, consequently, the set is a cyclic group. As a result, it is generated by a single element g(x) closely related to the constructor polynomial p(x). This can be illustrated by the following formula:
where i is called the exponential notation of the polynomial h (x).
We confirm that the change of the generator g(x) will lead to a fundamental change in the sign of the exponent, which will result in serious distortion of the entire encryption system.
The two algebraic operations will be defined from the two tables constructed to facilitate the calculations.
To facilitate the multiplication of F256 elements, it is recommended to use the two notations (Exp) and (Log). This technique is clarified by the equation below:
So, we can deduce the equation below
Please note that multiplication is closely related to the choice of generator g(x)
Every matrix used in this system are all in coefficients in F256
The multiplication of a size matrix (3,3) and a size vector (1,3) is determined by the following formula below
The determinant of a second order matrix is defined by the equation below.
This greatly increases the number of invertible matrices. We know that the number of invertible size matrix (p, p) in F256 is:
This proves that the brutal attacks on the matrices in F256 of higher order are remote.
III. INSTALL THE NEW CRYPTOSYSTEM
Throughout the document, the pixel intensity values of the color image pixels will be considered as elements of F256. Our method is articulated on the following points.
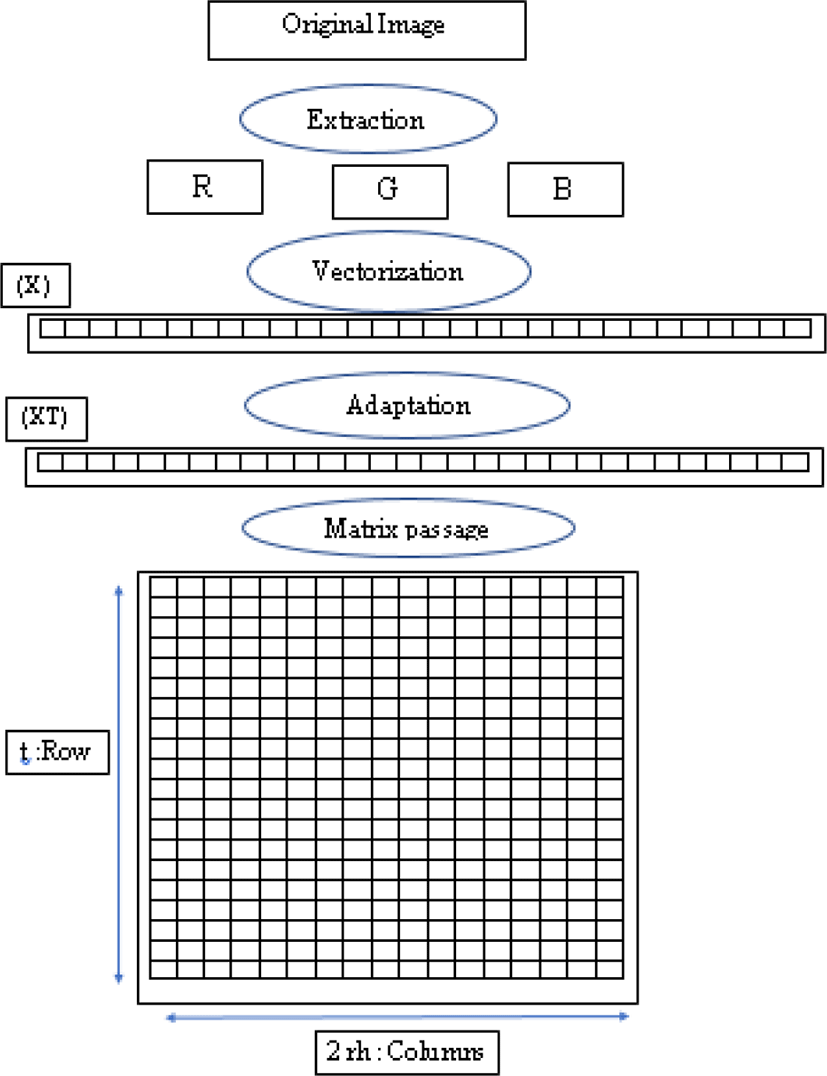
After extraction of the three color channels (RGB) and their conversion into vectors (Vr),(Vg),(Vb), a cohabitation is carried to form the vector X(x1,x2,… …..,x3nm). To apply Hill’s new method, the vector (X) must be cut into blocks of the size of (rh) calculated from the chaotic map and the original image size.
In order to implement the new technology, we need to cut the image vector (X) into large and small blocks (2rh). This operation follows the following formula:
The vector (X) must be imputed by (s) pixels by the following method:
We noticed that this decomposition is completely controlled by the decision vector (CR)
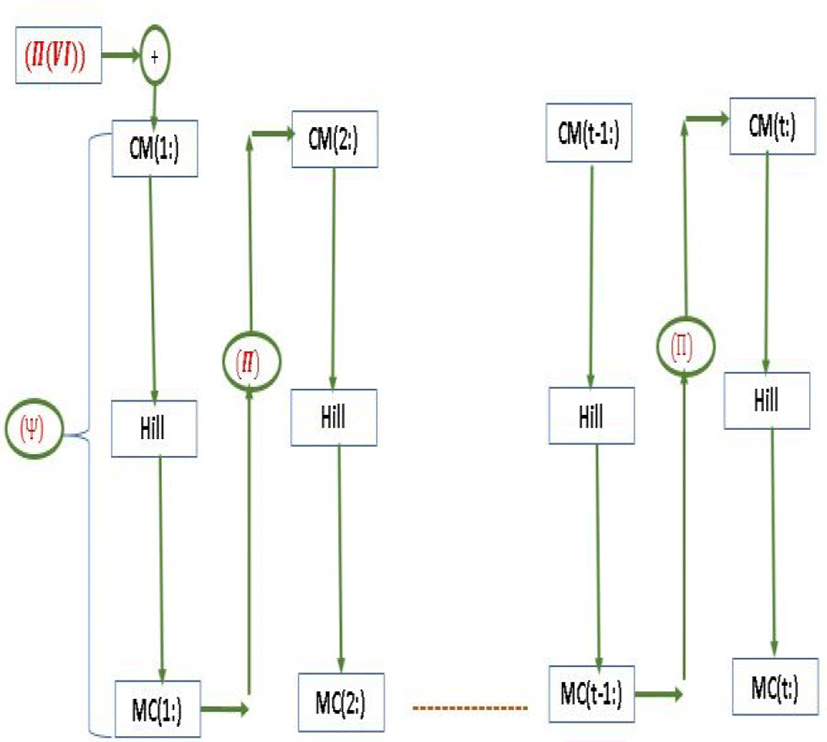
In parallel, convert two chaotic vectors (KR) and (KL) into matrices (MR) and (ML) of size (t, 2rh) following Fig. 2. After adjusting the size of the image vector, convert the latter to a matrix (MC) of size (t, 2rh) as shown in Fig. 3.
First, the(VI) initialization vector of size (1, 2rh)) must be recalculated to change the value of the starting block. Ultimately, the (VI) value is provided by the next algorithm
To surpass the uniform image problem (Black,White …) the setup value (VI) will be combined with the chaotic vector (TT) specified by the following algorithm.
The value calculated from the clear image and the chaotic map, will only be used to change the value of the start pixel and restart the encryption process.
IV. NEW IMPROVEMENT CLASSICAL HILL TECHNIQUE
The difficulty of reversing large matrices forces researchers to use matrices with sizes generally less than 5. However, due to linearity, classical HILL methods are still subject to statistical attacks. Our algorithm overcomes this anomaly by constructing an arbitrarily large invertible matrix, accompanied by chaotic vectors generated from the chaotic map used under binary chaotic vector control.
According to our technical steps, it will be easier to construct a large invertible matrix based on involute blocks and non-empty eigenvalue matrices
V. ORIGINAL IMAGE ENCRYPTION
After preparing the original image and constructing all the parameters, the following figure will explain the encryption process in detail.
(Π) Spread function, used to increase the impact of avalanche effects and protect the system from any difference. It is defined by the following formula:
VI. DECRYPTING THE ENCRYPTED IMAGE
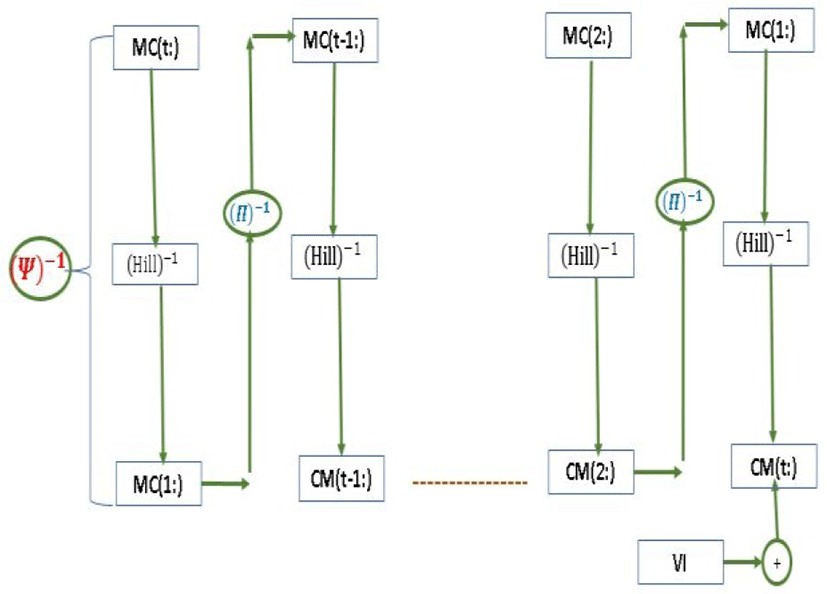
Our technique is a symmetric encryption system using a spread function, which forces us to start the decryption process from the last block to the first block, and then recalculate the initialization vector to extract the exact value of the first block. The figure below illustrates the decryption process
A decryption function can be described as:
VII. Simulation Result
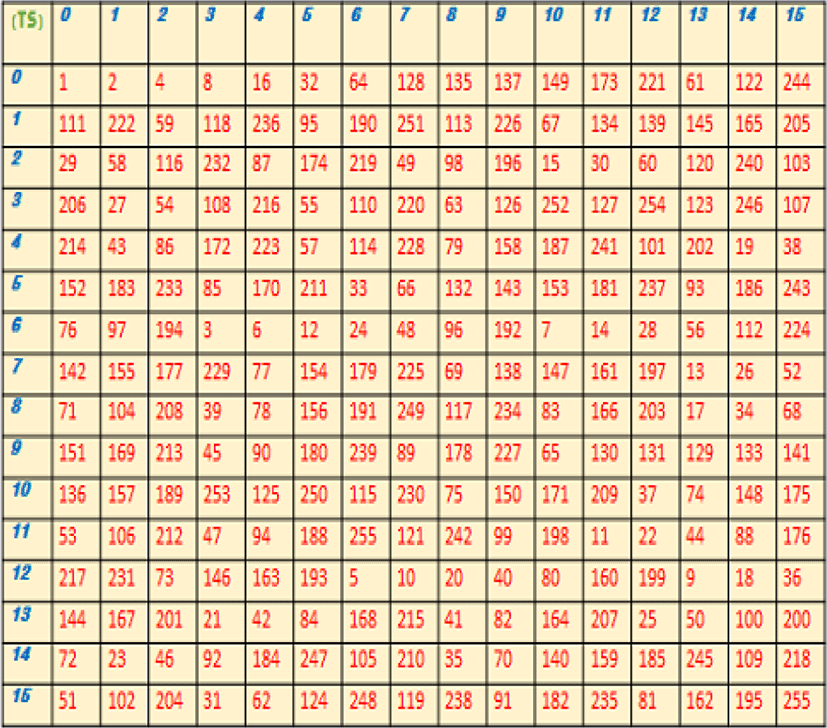
The polynomial p(x)=x8 + x7 + x2 + x + 1 is irreducible and eighth order on F [x], so it is a candidate for this study in the construction of the simulation body F256. In addition, the polynomial g(x) = x is a generator of such agents. Under these conditions, the (TS) dispersion index table is shown below.
Example:
So
By applying inverse permutation, a table of discrete logarithms can be derived from a table of discrete exponents. The two tables are used mutually in the field (F256).
So
In matrix notation,
So
VIII. INVESTIGATION OF CRYPTO SYSTEM PERFORMANCE
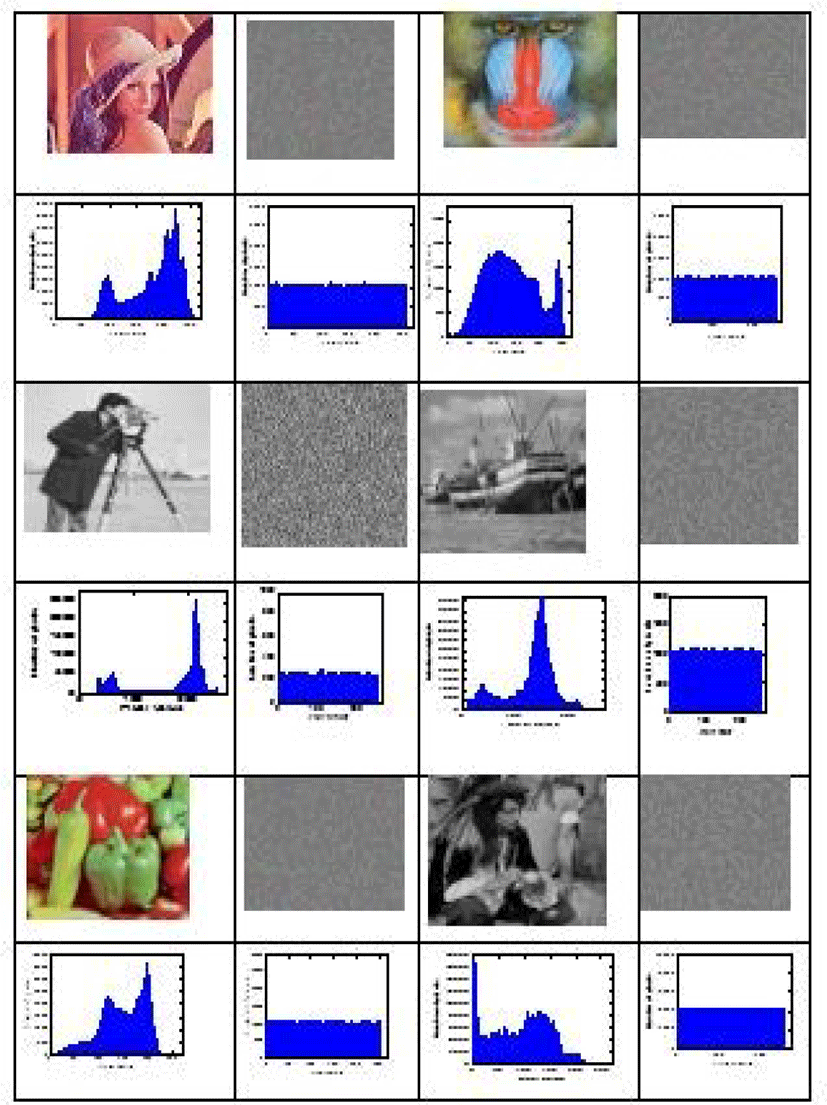
In this section, all the experiments were performed on a large color image database and using a corei7 personal computer, 16Gb memory, 500 Gb hard disk under the matlab software running under windows 7. Some of the most used reference images in cryptography and tested by our approach.
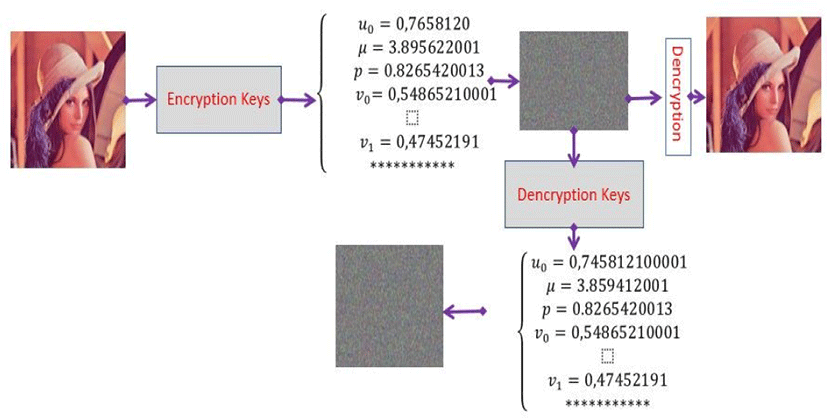
The high sensitivity of the encryption keys used in our system indicates that a very slight degradation of the encryption key automatically leads to an image that is so different from the original image. This confirmation can be viewed below the scheme in the next figure:
We note that a 10−15 change in a single encryption parameter of this technology is incapable of restoring the clear image by the same decryption process.
Our design has given a new opportunity to survive and to partner with the strongest members in the hope of rebuilding a new population more adapted to intruder aggression. To do that, we randomly selected an image and studied the strength of the original populations and the new generation, with the following results:
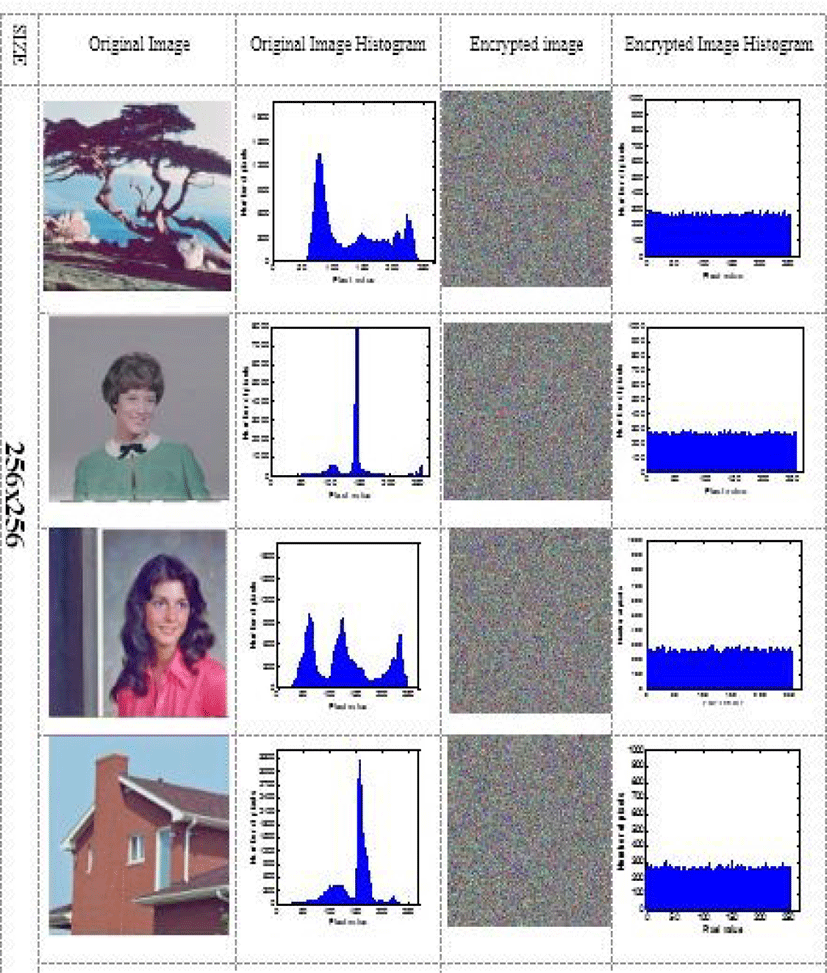
The histogram gives the distribution of the pixel intensity level of any original image passed under our algorithm, showing the concentration near certain intensity values and sometimes the maximum value, while the histograms of all encrypted images are uniformly distributed Yes, this eliminates any statistical histogram attacks.
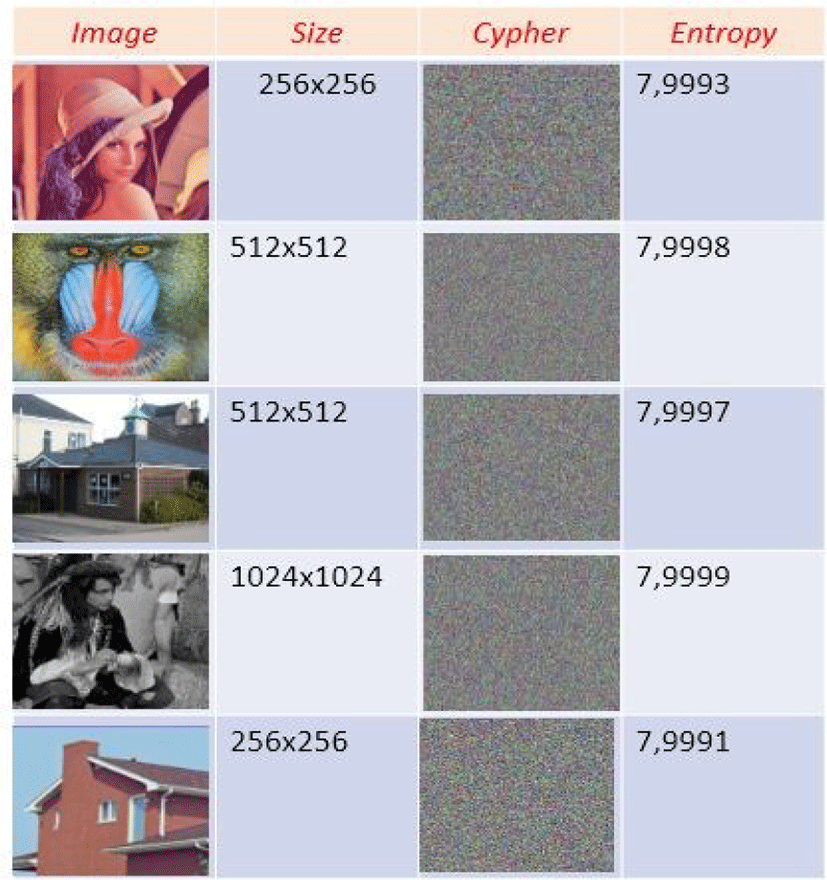
Entropy information is very important in measuring the randomness of the encrypted image. It is defined by the following equation: (MC) image of size (n,m), we pose(t = nm), so
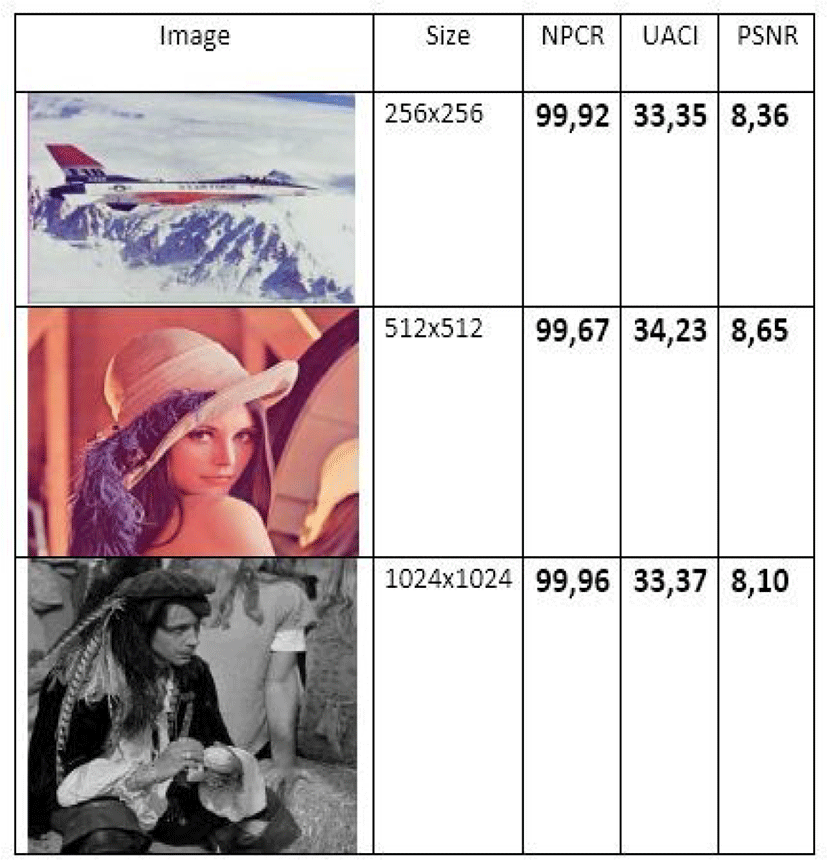
where p(i) is the probability of occurrence of level (i) in the image of the selected database. If H(MC) is close to the value 8 (8−bit coded image), the completely random aspect of the encrypted image is ensured. The following table illustrates the entropy of some reference images tested by our method:
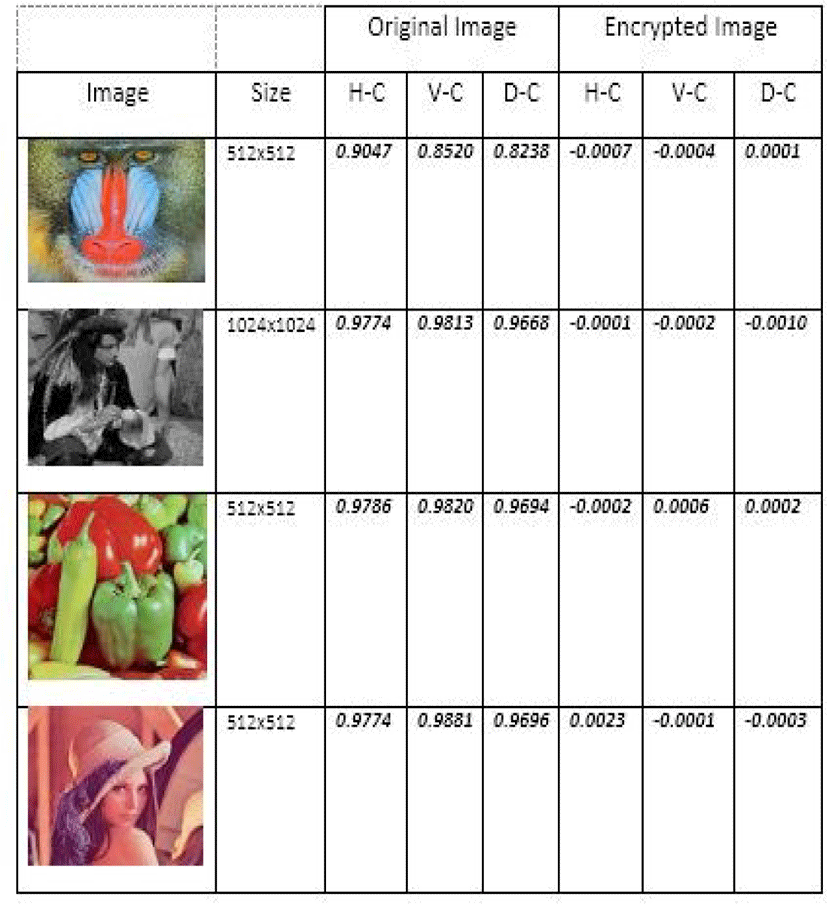
Let be two encrypted images, whose corresponding free-to-air images differ by only one bit, from (C1)and(C2), respectively. The expressions of these two statistical constants (NPCR)and (UACI) are given by equations below
The UACI mathematical analysis
Mean Square Error (MSE): This is the cumulative square deviation between the original image and other noisy images. When the MSE level decreases, the error also decreases. This constant measure the distance between the pixels of the clear image and the encrypted image. Calculated by the next equation.
where (P(i, j)): pixel of the clear image and (C(i, j)): pixel of the cypher image.
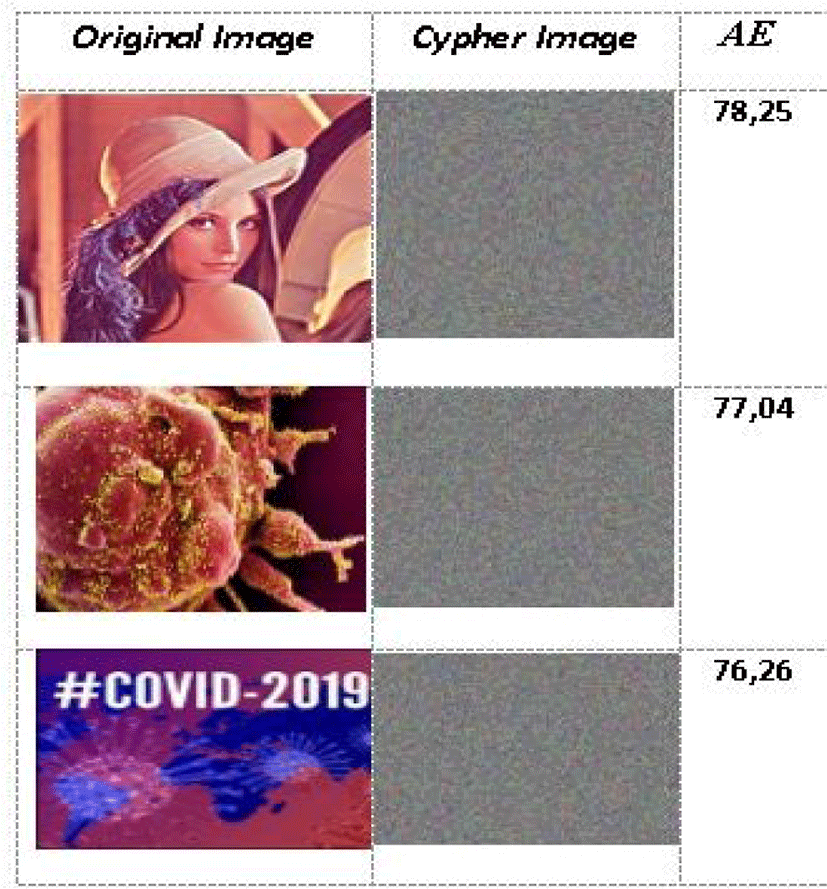
Our algorithm uses a strong link between encrypted pixels and pixels with clear policies. As a result, as data propagates through the structure of the algorithm, gradual changes become increasingly important. The avalanche effect is the number of bits that have been changed if a single bit in the original image is changed. The mathematical expression of this avalanche effect is given by
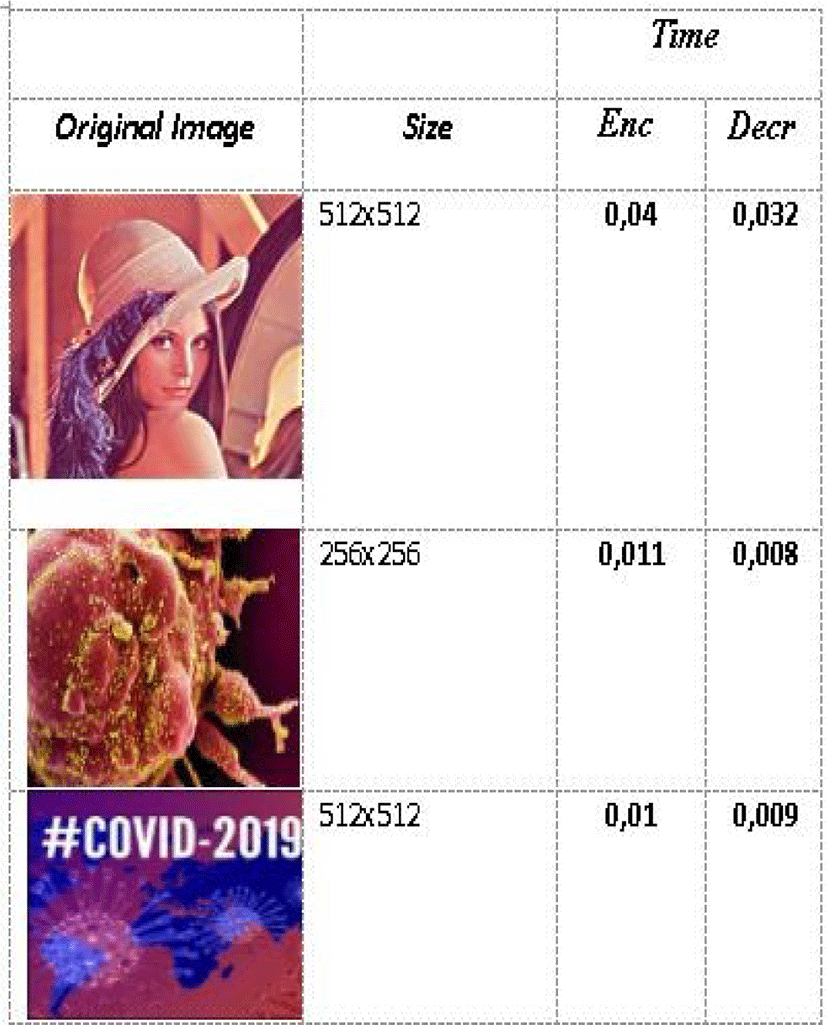
In our technique, the encryption and decryption times are very similar and vary in the interval [0.05, 0.1].
To approve and document the quality of our methodology in a timely fashion. And finally, thanks to these properties, we have selected the “Lena” grayscale image with three different sizes (256×256) (512×512) and (1024×1024). The results are presented in Table 9.
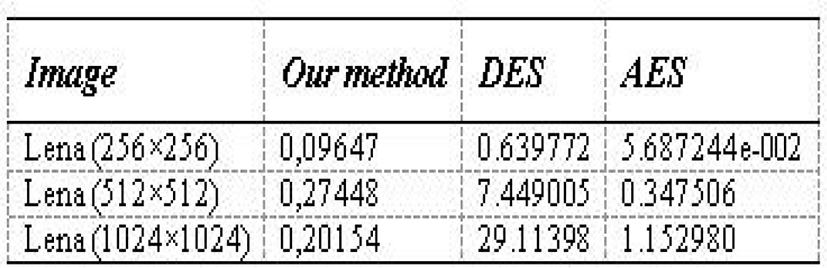
We compared the results with two classic algorithms, AES and DES, and can determine that the execution time is reasonable. The test was conducted on other images of different sizes, and we obtained an acceptable score. This is due to the low algorithm complexity of the algorithm implemented in our strategy.
IX. MATH SECURITY
Our algorithm uses a large symmetric key that is extremely sensitive to initial conditions and control parameters. This ensures that small interference in the key will regenerate a new subject and a new calculation table. In addition, the complexity of using discrete logarithms in calculations increases the difficulty of attacking our systems. The construction of the key matrix is closely linked to the chaotic maps used, which eliminates any brutal attacks.
X. CONCLUSION
Hill’s conventional system is very easy to install in the color image encryption system, as long as the inversion matrix is determined in the carefully selected ring. But due to linearity, this technique is still vulnerable to statistics and brute force attacks. Carried on instead of the classic Z/256Z ring. Similarly, the construction of a large-sized invertible matrix has been introduced based on the involution block, and the non-zero eigenvalue matrix has been described in detail. The large number of matrices built in this way ensures better protection against any brutal attack. Using logarithms and discrete exponents and translation vectors to overcome linear problems will increase the complexity of our method.