I. INTRODUCTION
RFID technology is an identification technology that attaches tags to objects to transmit and process information about objects and the surrounding environment by radio frequency. The use of RFID technology is changing frequently these days, and their use is widespread [1].
The anti-collision algorithm for identifying multiple tags in the RFID system is largely classified into a probabilistic and a deterministic method [2], [3], [4]. The probabilistic method uses FSA (Frame Slotted ALOHA) algorithm based on ALOHA method, which is adopted as standard in EPCglobal Class-1 Gen-2 and ISO/IEC 18000-7 [5], [6].
In ISO/IEC 18000-7, the tag collection process is organized into a series of tag collection rounds [6]. A tag collection round is divided into a listen period and an acknowledgement period. The tag collection round begins with the collection command transmitted by the reader. Tags that have received the collection command randomly select a slot in the listen period and transmit a response including their identification codes. The reader transmits the read command to the tags that have received the collection response without collision, receives the data, and transmits a sleep command to the tags. The identified tags in this process have a problem of consuming energy because they must remain in the waiting state until they receive a sleep command. Therefore, in this paper, we propose a modified tag collection algorithm to reduce the energy consumption and identification delay due to the sleep command. In the proposed method, the collection response result of the previous collection round is included in the collection command. And the identified tags are transited to the sleep state without an implicit sleep command.
This paper is organized as follows. In Section II, we describe the tag collection algorithm in ISO/IEC 18000-7. In Section III, we propose a simplified tag collection algorithm. Section IV shows the simulation results, and Section V concludes the paper.
II. RELATED WORKS
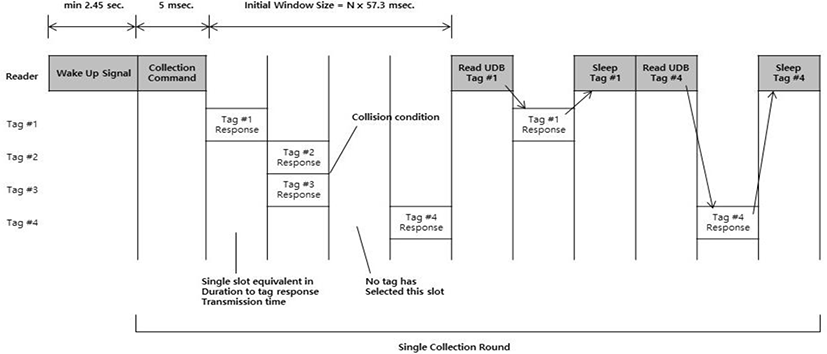
ISO/IEC 18000-7 is a representative active RFID system standard that defines air interface communications between a reader and a tag in the 433MHz [6]. Fig. 1 shows the timing diagram for the tag collection algorithm defined in the standard. As shown in the figure, the reader transmits a wake-up signal before the tag collection procedure. The tags that have received the wake-up signal transit to the ready state and wait for the collection command from the reader.
In ISO/IEC 18000-7, the reader broadcasts a collection command to start a collection round. The collection command broadcasted by the reader provides information such as window size and a maximum packet length. Those fields are used as information for calculating the slot size and the number of slots of the listen period. The tags in the ready state receive the collection command and calculate the size of the listening period, the time slot size, and the number of time slots. Based on the calculated time slot information, each tag selects a random time slot for its response, delays its response until the start of the selected time slot. On the other hand, the reader waits for the response of the tag in each slot [6], [7].
After the listen period, the reader performs an acknowledgement period for collecting additional data on the tags that have successfully identified. For each tag from which the reader received a valid collection response, the reader sends a point-to-point read command to retrieve any remaining data from the tag. And then the reader sends a point-to-point sleep command to the tag. The tag receiving the sleep command transits to the sleep mode to reduce power consumption. A tag that transitions to sleep mode does not respond to further commands from the reader until it receives a wake-up signal. This process continues until no tags were identified and no collisions were detected [8].
As described above, a series of <collection command, collection response, read command, read response, sleep command> transmission is repeatedly performed in the tag collection in ISO/IEC 18000-7 standard. In the standard specification, the read command and the sleep command take 7.176msec and 5.88msec, respectively. There is a problem that identification delay occurs due to the transmission of the read command and the sleep command for all the tags identified in the listen period.
III. PROPOSED ALGORITHM
This section proposes a new tag collection algorithm to improve the identification delay caused by the read command and the sleep command in the tag collection procedure of the standard described in Section II. In the proposed algorithm, the response to the previous collection round is included in the collection command. And the tag acknowledged through the collection command enters into the sleep mode without a separate sleep command.
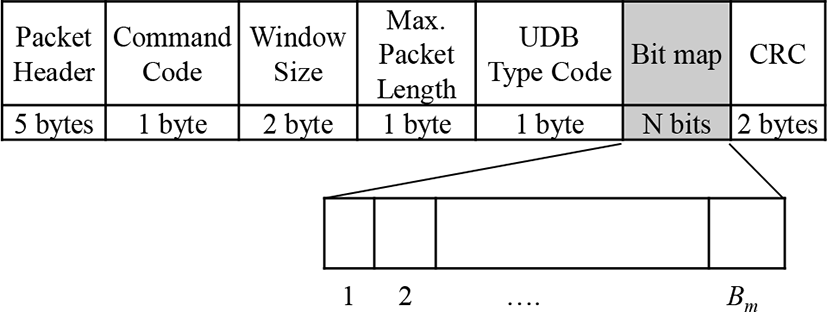
Fig. 2 shows the modified collection command for the proposed collection algorithm. The modified collection command includes a bitmap indicating the success of each slot of the previous collection round. The length field indicates the number of previous slots. The bitmap is set to ‘1’ if the corresponding slot of the previous collection round is successfully identified, and to ‘0’ if the slot is collided or empty.
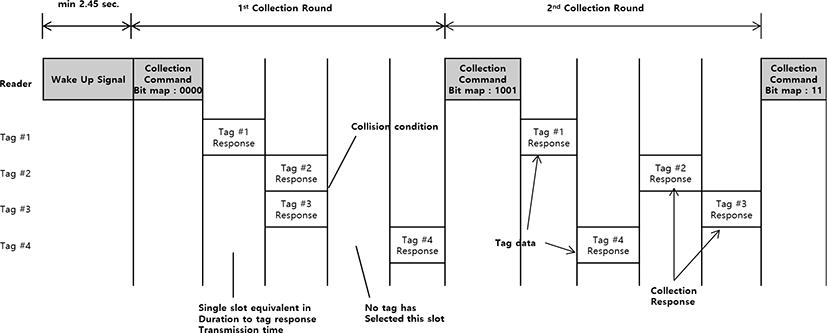
Fig. 3 shows an example of the tag collection procedure proposed in this paper. All bitmaps for the first collection command are set to ‘0’. The tag that receives the collection command selects an arbitrary slot to transmit a collection response, and waits for the next collection command. The reader transmits a collection command that sets a bitmap for the slot successfully identified in the previous round, and receives tag data as many as the bitmap value is ‘1’.
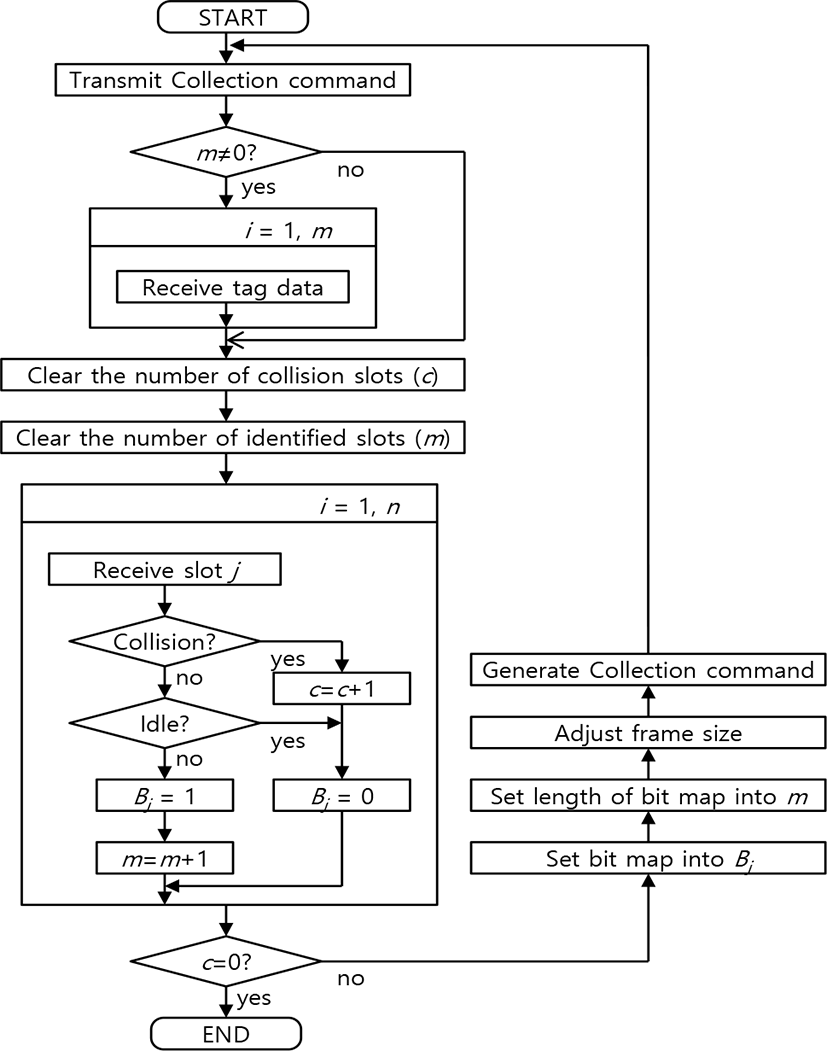
The operation of the reader for the proposed algorithm is shown in Fig. 4. As shown in the figure, the reader receives as many tag data as the number of slots (m) successfully identified in the previous round. The reader also sets a new bitmap value based on the collection response for all collection response slots (n). The tag that sent the collection response command waits for a new collection command. If the bitmap value of the slot number (j) selected in the previous round is ‘1’, it is a case that the collection response is successfully transmitted. In this case, the number of bits set to ‘1’ is accumulated up to the slot number selected by itself, which becomes the data slot number to which the additional data is to be transmitted.
IV. SIMULATION RESULTS
The performance of the proposed algorithm is compared with the ISO/IEC18000-7 standard through simulation. In the physical layer specifications of ISO/IEC18000-7 standard, the bit duration for all command is defined as 0.036msec. Therefore, the parameters presented in Table 1 are defined in the same way as the standard [6]. The number of tags was increased from 10 to 500 by 10. And the average of 1,000 iterations for each tag was used as the simulation result. Also, the number of tags remaining in each collection round is estimated, and slots of the next round are allocated based on the estimated number of tags.
| Item | Value (msec) | |
|---|---|---|
| Standard | Proposed | |
| Wake-up signal | 2,450 | |
| Collection command | 5.232 | 6.528 |
| Collection response | 7.812 | |
| Read command | 7.176 | - |
| Tag data | 40.212 | |
| Sleep command | 5.880 | - |
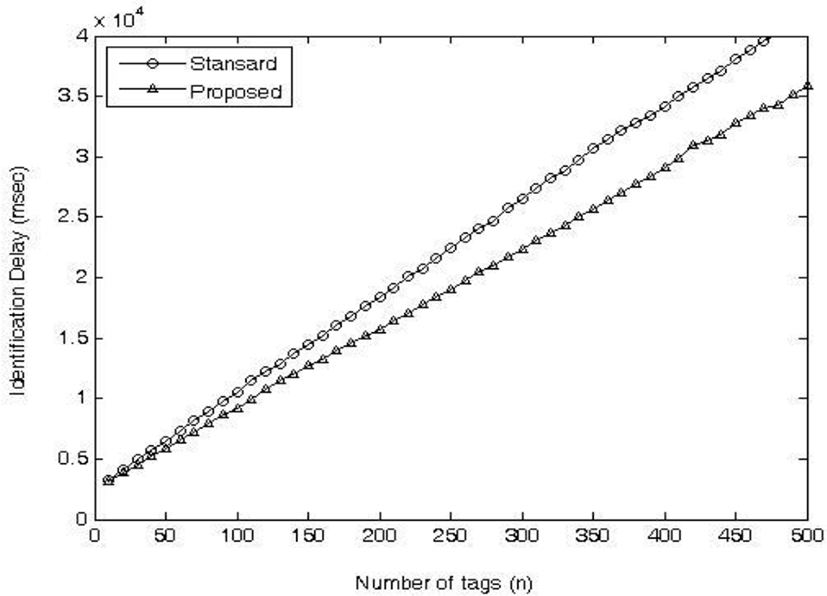
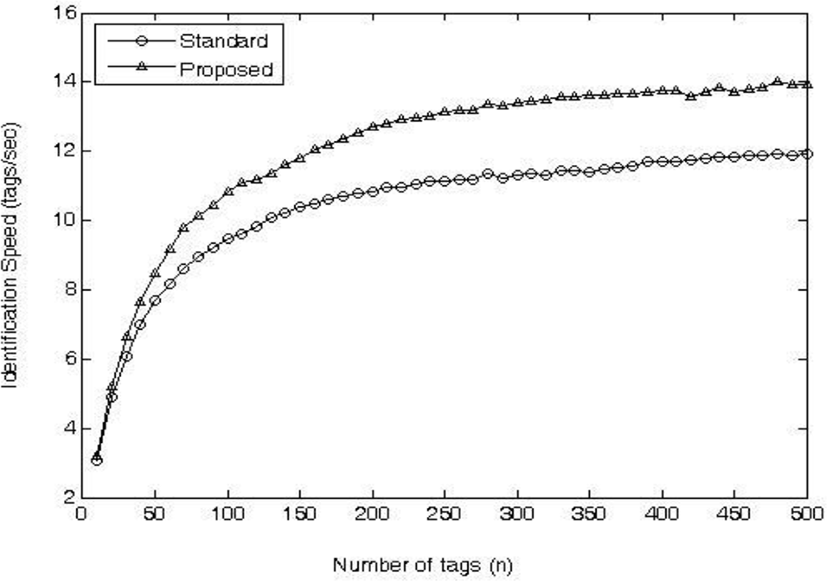
Fig. 5 and 6 show the identification delay and speed, respectively, according to the number of tags. The identification delay means the time required to identify all the tags, and the identification speed means the number of tags identified per second. The standard takes 26,495msec to identify 300 tags, and the proposed technique takes 22,346msec. Therefore, the proposed scheme is identified about 16% faster than the standard scheme. Also, in the case of the standard, 10.5 tags per second are identified, and in the proposed method, 12.1 tags are identified on average. The proposed algorithm can improve the identification speed by about 15% compared with the standard.
In the standard, the read command and the sleep command are transmitted to the identified tags in the AP period. This causes a delay for the identified tag to transition to the sleep mode. On the other hand, in the proposed algorithm, the reader broadcasts the information about the tag identified in the previous round to the tags in the bitmap format while transmitting the collection command. The identified tags transmit their additional data in the corresponding data slot and transit to the sleep mode.
V. CONCLUSION
In this paper, we proposed a simplified tag collection algorithm to improve tag collection performance in IEC / ISO 18000-7, the standard of active RFID systems, and analyzed its performance. In the proposed method, the collection command was modified to include the response result for the LP section of the previous collection round in the collection command. Also, the tags that received the collection command confirmed the result of their collection response, and transmitted additional data without a separate sleep command from the reader. As a result of the performance analysis, the proposed method was able to obtain superior identification delay performance compared to the standard because tags that succeeded in collecting response do not wait for separate read and sleep commands from the reader.