I. INTRODUCTION
We live in a society where anytime, anywhere can be connected with the touch of a finger. People are connected, people are connected, things are connected. Artificial intelligence and big data analytics technologies are combined with IoT to bring incredible innovation and change. This factor of change is particularly possible thanks to the data. In recent years, the paradigm of the global economy has shifted to the data economy. The data economy is a system that creates new added value based on data assets. Data is a source resource that enables innovation in all areas, including big data, artificial intelligence, autonomous vehicles, smart factories, and smart healthcare. Among data, personal data is a key asset in the data-driven economy. Korea recently revised the Privacy Act in January 2020 to ensure the use and protection of personal data in order to secure the initiative in the data-driven economy [1]. These changes in the environment will require data subjects to find new balances in advancing the data economy without losing control over their personal data and to seek win-win strategies for both data subjects, data controllers and data users.
To do this, data subjects, data controllers, and data users all need a way to securely manage their personal information. However, the higher the utilization of personal information, the higher the risk of personal data infringement. State agencies and private companies use personal data to increase the use of personal data to deal with complaints or to pursue revenue through marketing. However, the risk of personal data infringement is increasing due to lack of awareness or mistakes of personal data handlers. According to the Korea Internet Agency, about 159,255 personal data infringement reports were received in 2019, and even after entering in recent years, personal data leakage and abuse cases have continued to increase [2]. Due to such accidents related to personal information, at the corporate level, we are experiencing cost expenditures due to legal disputes and the deterioration of corporate credit, and personal data is used indiscriminately at the individual level as well. Accordingly, the number of cases of damage such as invasion of privacy and phishing is increasing. In order to reduce the damage caused by such careless handling of personal information, the government is continuously strengthening public relations for changing awareness of personal data protection. Is committed to the security protection of personal data managed by public institutions. Institutions and companies have long recognized the importance of protecting personal data and, in order to manage it continuously, have introduced a certification of various personal data management systems such as ISMS-P (Personal Information and Information Security Management System) [3] and ISO27002 [4] to build a risk management system. It was However, even if a systematic management system of personal data protection is established at the organizational level, some members of the organization neglect the management of personal information, lack of consciousness, intentional leakage of personal information, etc. When an accident occurs, it becomes a big problem. The theory-based education and paper-based personal data breach response training do not greatly help raise awareness among members of the organization. In this paper, we design and propose a framework for assessing responsiveness to personal data breaches based on Capture-the-Flag. Capture the Flag (CTF) is a game that challenges problems composed of complex scenarios and is a useful way to solve many problems of engineering or fusion [5]. The Problem Method scenario is designed using the various types of privacy breaches that have occurred over the past five years, as well as indicators of ISMS-P and ISO29151 [6]. The framework for evaluating personal information infringement response based on Capture-the-Flag is an educational design plan aimed at helping anyone to easily detect signs of personal information infringement and increase the ability to respond quickly to accidents. In this research, we analyze the processing pattern of personal data managed by the organization, detect signs of abnormality, and can easily handle personal data leakage and abuse in advance, personal data leakage response training platform I will try to present you about the design proposal. In order to design such a framework for assessing responsiveness to personal data breaches based on Capture-the-Flag, we first identify the risks that may occur in connection with personal data leakage and identify the root causes that can cause the risk. We will try to define the important risk factors, and how to create important risk indicators that can be managed by quantifying the important risk factors. In particular, by giving an example of the main risk indicators related to the leakage of personal data and presenting them so that they can solve problems for each processing step and processing difficulty, the technical management of the organization for personal data protection It presents about the method that can implement the protective measures as a concrete system.
II. THEORETICAL BACKGROUND
Personal data defined in the Personal data Protection Act refers to information that can identify an individual by using information that can be recognized by a living person, such as name, social security number, and video, or by using additional information that can be easily combined. The classification of personal data was classified into four stages, as shown in Table 1, by evaluating whether the person was identified and the risk of infringement [7].
| Rating | Level of Personal Identification | Level of Infringement risk | List of Personal Data |
|---|---|---|---|
| 1 | High | High | Resident registration number, Alien registration number, Passport number, Driver’s license number, Credit card number, Bio information (face, iris, fingerprint, vein, etc.) [8] , Consultation details, Location information, IP information, Personal video information, System (homepage) usage details, etc. |
| 2 | General | High | Name, Address, Phone number, Mobile phone number, Email address, etc. |
| 3 | Low | High | Race information, Religion information, Military service, Social group activities, Health information, etc. |
| 4 | Low | Low | Pseudonymized Data, General information (no personal information) |
ISO/IEC29151 [9] defines control objectives, controls and control guidelines to meet the requirements identified by the risk and impact assessment associated with the protection of personally identifiable information, based on ISO/IEC 27002. The system applies to both public and private companies, government agencies and non-profit organizations that process personal information. Personal Information and Information Security Management System (ISMS-P) [10] is a system suitable for Korea based on the international standard ISO27001 and ISO29151. This system is a system that the Korea Internet & Security Agency investigates and certifies that the organization’s personal information protection and information management system is properly established and operated.
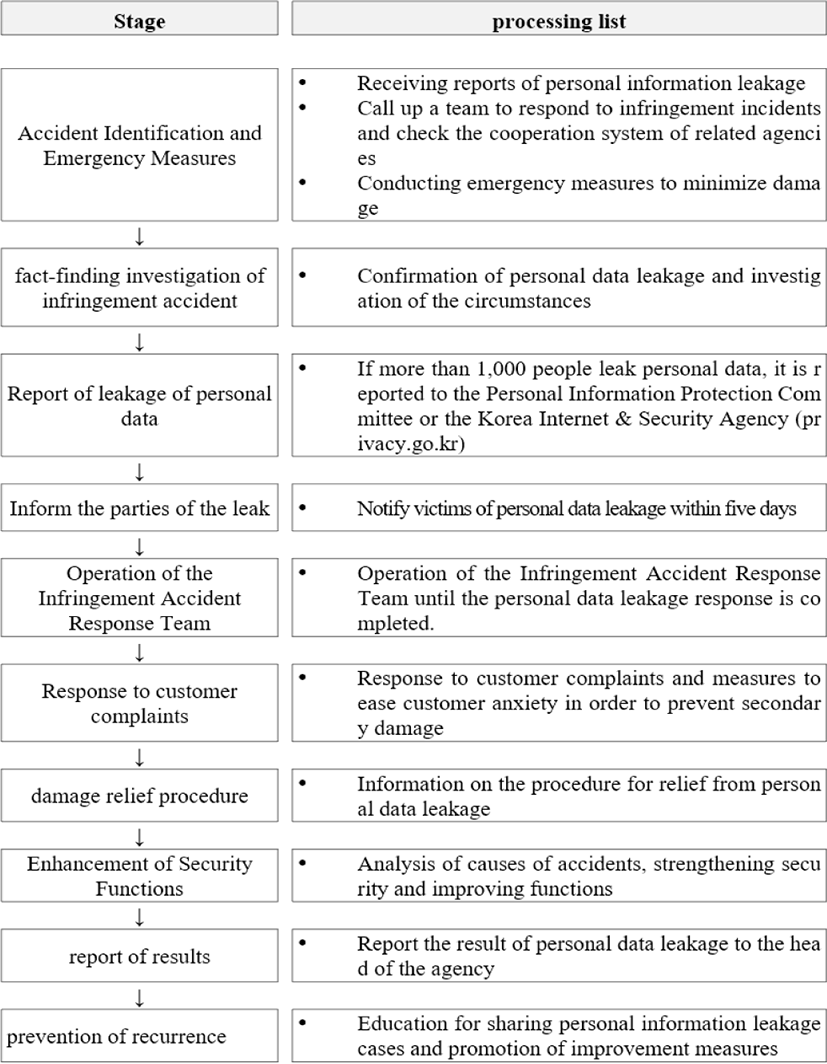
In the event of a personal data breach, respond step by step as shown in Figure 1 [11].
The major infringement incidents of personal data from 2018 to 2020 are shown in Table 3. Most of the cases were found to have been caused by poor management and lack of awareness of personal information handlers.
| Year | Case | Content |
|---|---|---|
| 2018 | Google Plus: 52.5 million major privacy breaches [12] | Two software vulnerabilities in Google Plus have resulted in 52.5 million major privacy breaches |
| 2018 | Marriott Hotel: Approximately 500 million customer data exposures [12] | The Marriott Hotel had an accident in November 2018 in which about 500 million customer data were exposed. |
| 2018 | Facebook: Software bugs [12] | Software bugs have occurred, exposing 70 million users' information |
| 2020 | A number of local authorities in Korea: Information leak of infected persons with the COVID-19 [13] | Disclosure and leakage of route information of COVID-19 infected persons due to lack of awareness and error by the person in charge. |
| 2020 | Local government in jeju: Failure to comply with restrictions on processing unique identification information [14] | 70,000 people's personal information is exposed because the person in charge of personal data does not enforce unique identification processing restrictions |
So far, various curricula and simulations have been conducted to prevent the leakage and outflow of personal data from state agencies and a number of corporate-level applications. However, as the education system adopted a one-sided education system centered on legal compliance and theory, it lacked awareness of personal information handling and the personal information handler was always at risk of infringement. Simulated response tests based on virtual scenarios are limited to the participation of only some of the agencies and personnel who have personal information, and many of the personal information handlers do not understand the procedures for personal information infringement and thus cannot handle accidents quickly. To overcome this, this study proposes the design of framework for assessing responsiveness to personal data breaches based on Capture-the-Flag.
III. DATASET ANALYSIS AND PLATFORM DESIGN PROPOSAL
A response assessment framework for assessing responsiveness to personal data breaches based on Capture-the-Flag is proposed as shown in Figure 2. The proposed framework was divided into stages 1 to 3 by difficulty. Level 1 is a sub-level question that measures basic concepts such as the definition of personal data and general legislation. Level 2 is designed as a virtual environment in which management methods and technical, administrative and physical security measures for systems collecting personal data can be practiced to help them understand the process of personal data processing at an intermediate level. Level 3 focuses on developing the ability to quickly respond to various personal information breaches at the top level. At this stage, it is designed as a problem-solving method to learn how to take action at a high level for fault results measured by standard indicators such as ISMS-P, ISO27001, ISO29151.
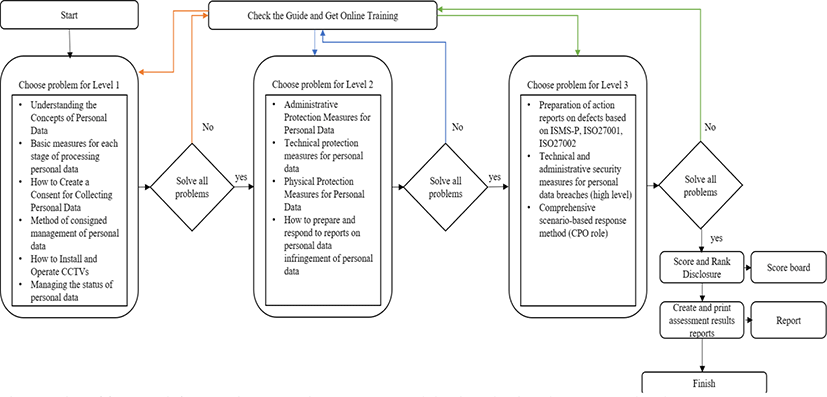
All the problems given to each level were solved so that they could move on to the next level, and if they did not pass, they had to study online education courses and guides to give feedback. Ranking is given based on processing completion time. Through all stages, the overall score and ranking could be checked, and the evaluation results could be checked and printed by item.
The problem types of the personal information infringement response assessment platform for problem solving methods are as shown in Table 4, and the composition is divided by difficulty level. Based on the casebook published by the Personal Information Protection Commission (2012-2018) [15] and the casebook for personal information protection evaluation between 2013 and 2017 [16], data by case were collected and analyzed. Defect cases based on the results of the ISMS-P [17] certification review by local governments were classified as cases and designed as a solution to the problem [18]. The scoring criteria for each question were given one point, and the measurement methods were multiple choice and practical.
IV. CONCLUSION
We have conducted various curricula and mock training to prevent the leakage and outflow of personal data. As the education system adopted a one-sided education system centered on legal compliance and theory, there was a lack of awareness of the handling of personal information, and the personal information handler was always at risk of infringement. Simulated response training is also conducted based on virtual scenarios, with only part of the agencies and personnel holding personal information participating. As a result, many personal information handlers are unable to handle accidents quickly because they do not understand the procedures for personal information infringement.
In this study, we proposed the design of CTF game-based personal information leakage response education platform that can analyze the processing patterns of personal information managed by the organization, detect anomalies, and easily handle leakage and abuse of personal information in advance. The platform focused on understanding the possible risks associated with personal data breaches, identifying the root causes of risk induction and strengthening the ability to resolve them on its own. In particular, it is expected that organizations and managers in charge of personal data protection will help by guiding and presenting major risk indicators related to personal data leakage through a web-based platform to solve problems by processing stage and level of difficulty. In future research, we would like to establish a proposed training and training platform and conduct empirical research on institutional personnel.